How to Improve Your Smart Home Security: Expert Tips for Safeguarding Your Connected Devices

As the world becomes increasingly connected, smart homes are becoming more prevalent, providing us with convenience, comfort, and automation. However, with the benefits of this advanced technology comes the need to address potential security risks. The rise in Internet of Things (IoT) devices has opened new avenues for cyber threats and unauthorized access, making it crucial for homeowners to prioritize smart home security.
In this article, we’ll explore practical strategies and expert recommendations to bolster the security of your smart home. We’ll delve into the primary concerns surrounding smart home vulnerabilities, such as weak passwords, outdated firmware, and unsecure wireless networks. Moreover, we’ll discuss effective measures to safeguard your smart devices and your privacy.
By implementing the strategies discussed in this guide, you can protect your smart home against potential threats, ensuring a safer and more secure living environment for you and your family.
Table of Contents
Do Smart Homes Need Security?What Can Cybercriminals Do If They Get Access to My Home Network?
Disconnecting a Smart Home Device
How Can I Improve the Security of My Smart Home?
Smart Home Privacy – Best Practices
Centrally Managed Smart Homes: Balancing Convenience and Security
Final Thoughts on Strengthening Your Home Security System
FAQ
Do Smart Homes Need Security?
Yes, smart homes are increasingly vulnerable to cybercriminals due to the growing number of internet-connected devices.
Smart home security is an essential consideration as cybercriminals can take advantage of weaknesses in smart home devices, which may result in unauthorized access to sensitive data or even complete control of the device. For example, a hacker could gain access to your smart lock and unlock your front door, or they could listen to your conversations through a hacked smart speaker.
This table showcases smart home devices and their data collection capabilities.
| Device | Data collection | Who is this data shared with? | Who is this data shared with? |
| Doorbell | Collects images and videos, real-time recordings, personal information | Third-party partners, data brokers | Access the recorded data, gather personal information for identity theft or blackmail |
| Smart light bulbs |
Energy consumption data, on/off patterns, dimming, and color settings | Third-party partners, data brokers, smart home platforms | Turn all of the lights on in the home or facility to overload the power system |
| Locks |
Location, IP address, photos, videos, user activity | Landlords, police | Take control of who gets in or out of the house or facility |
| Smart cars |
Location, route data, media, contacts, emails, messages | Government, car companies, data brokers | Eavesdrop sensitive data or inject malicious commands, GPS spoofing |
| Smartwatch |
Biometric data, activity tracking | Health and fitness service providers, mobile device and OS providers, smartwatch manufacturers | Spoof other devices connected to the watch and steal user data |
| Voice assistants |
Audio recordings, voice data, purchase information | Amazon, Google, Apple, third-parties, data brokers | Play your voice commands or steal voice data as credentials for other voice command systems |
| Speakers |
Always listening, records when falsely triggered, audio recordings | Amazon, Google, data brokers | Voice spoofing, eavesdropping, unauthorized access |
| Smart thermostats |
Collects temperature and data usage | Energy management companies | Allow attackers to manipulate thermostat settings, extract data directly from the device, manipulate its settings, or install malicious software |
| Robot-vacuums |
Vacuum path maps, cleaning scheduling | GManufacturers, data brokers | Steal information like the home’s layout or monitor residents’ activities |
| TV |
Viewing history, device type, email, location, personal preferences | Social media marketing companies, advertisers, data brokers | Unauthorized access to personal information such as email id, password, bank details, personal viewing habits, etc |
| Security cameras |
Location data, video footage | Device manufacturer, cloud storage provider, authorities | Unauthorized access to live video feeds, recorded footage, or personal information. |
| Smart coffee machine |
Strength, temperature, serving size, timestamps, frequency, time of day, cleaning cycles, water levels | Device manufacturer, third parties | Disrupt the brewing process or issue commands resulting in breaking the device completely |
| Smart appliances |
Usage data energy consumption | Device manufacturer third-party service providers, analytics or advertising companies | Remote control over the appliance’s functions, unauthorized access to usage patterns |
| Smart workout mirrors |
Age, height, weight, heart rate, location, audio, video | Marketing companies | Potential exposure and manipulation of personal workout data and routines |
| Refrigerator |
Food inventory, shopping habits | Third parties, data brokers | Order as many groceries as possible, ruin the food by changing the temperature settings |
| Smart beds |
Heart rate, sleep pattern data, respiration | Mattress companies and their partners | Control bed settings, exposure to health-related information, sleep tracking |
| Smart toilets |
Flush frequency and duration, water pressure, temperature settings, sensor data | Product manufacturer | Waste water by controlling the bidet and flush functions |
| Smart toys |
Geolocation data, interaction data, personal information, audio and video recordings | Toy manufacturers or connected apps for interactive features or analytics | Spy on or interact with the child playing with the toy |
| Home gateways |
Device information, network traffic, user authentication data, activity log, remote access permissions | Gateway manufacturer, ISP, third-party services for network management, security, or analytics | Control connected devices remotely or redirect connections toward hidden malicious behaviors |
What Can Cybercriminals Do If They Get Access to My Home Network?
If cybercriminals gain access to your home network, the implications can be severe, as they can control and manipulate various aspects of your smart home system.
Below are some of the potential consequences of a compromised home network:
| Consequences | Explanations | Examples |
| 🔏 Privacy invasion | Cybercriminals can access your personal information, eavesdrop on your conversations, and even watch your activity through smart cameras or voice assistants, significantly invading your privacy. | In 2019, a family in Florida reported hackers had accessed their Nest security camera and spoke to them through the device. |
| 🥷 Data theft |
Hackers can access your sensitive data, such as financial information, login credentials, and personal documents, leading to identity theft and other forms of cybercrime. | In 2017, the CloudPets breach exposed voice recordings and personal data of more than half a million people. The data leak also included email addresses and passwords |
| 🎛️ Device manipulation |
By gaining control of your smart devices, cybercriminals can manipulate their functions, such as altering the temperature settings of your smart thermostat, locking or unlocking smart doors, or tampering with security systems. | In 2019, a hacker took control of a couple’s smart home system in Wisconsin, raised the thermostat to 90 degrees and started playing explicit music through their smart speakers. |
| 💰 Ransomware attacks |
Hackers can infect your smart home devices with ransomware, rendering them unusable until you pay a ransom. This type of attack can cause significant disruption and financial loss. | In 2020, Garmin, a company producing GPS devices and smart wearables, experienced a ransomware attack leading to a multi-day outage of its services, causing significant customer disruption. |
| 🤖 Botnets |
Cybercriminals can hijack your smart devices and use them as part of a botnet, a network of compromised devices used to launch large-scale cyberattacks, such as distributed denial of service (DDoS) attacks. | In 2016, the Mirai botnet, consisting of compromised IoT devices, launched a massive DDoS attack on the DNS provider Dyn, causing widespread internet outages. |
| 🕵️ Surveillance |
Compromised devices can enable hackers to spy on you, gather information about your habits and routines, and use it for targeted phishing attacks or other malicious activities. | The Ring doorbell controversy revealed concerns over privacy and surveillance are warranted, as the company gave law enforcement access to customers’ video footage without explicit consent. |
In short, the implications of a hacked smart home can be significant, ranging from loss of privacy to physical security risks. By taking proactive steps to secure your devices and network, you can protect yourself from these threats and enjoy the convenience of a smart home without compromising your security.
Disconnecting a Smart Home Device
Disconnecting a smart home device is sometimes necessary to address security risks and regain control over privacy. With the increasing interconnectivity of these devices, they can become easy targets for hackers, compromising your personal information and even allowing unauthorized access to other devices on the network. By disconnecting a compromised device, you can help protect your privacy and security.
This allows you to have greater control over your personal information. By evaluating the risks and benefits of each device, disconnecting when necessary enables a safer and more privacy-conscious smart home environment.
How Can I Improve the Security of My Smart Home?
Improving the security of your smart home is essential to protect your personal information. Here’s how you can enhance your smart home’s security:
- Always change default usernames and passwords
When you set up your smart devices, always change the default usernames and passwords. Default credentials are easily available online, making them an easy target for hackers.
By using strong, complex passwords incorporating a combination of letters, numbers, and special characters, you can significantly enhance the security of your devices. Regularly updating these passwords further mitigates the risk of unauthorized access and helps maintain the integrity of your smart home ecosystem.
Below are the step-by-step instructions on how to change the password on your smartwatch:
- On your smartwatch’s home screen, navigate to the settings menu by tapping on the settings icon.

- Once in the settings menu, look for the Passcode option and select it. This will take you to the passcode settings screen.
- On the passcode settings screen, you’ll receive a prompt to enter your current passcode for verification purposes.
- After entering the current passcode, you’ll now have the option to change the passcode. Select the Create New option
- A new screen will appear where you can enter your desired new passcode. Once you have entered the new passcode, confirm it by entering it again in the designated field
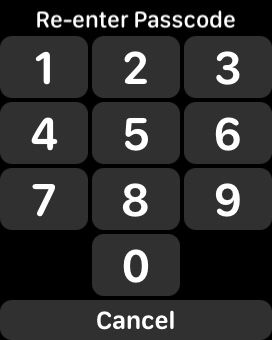
- Finally, select the Done button to apply the new passcode settings to your smartwatch
By following these steps, you can successfully change the passcode on your smartwatch, enhancing its security and protecting your personal information.
- Enable two-factor authentication (2FA)
Two-factor authentication adds an extra layer of security by requiring you to provide a secondary form of identification, such as a text message or fingerprint, in addition to your password. Enable 2FA whenever possible.
By enabling 2FA on your smart home devices and associated accounts, you ensure even if an attacker gains access to your password, they still need the secondary authentication factor to gain entry. This greatly reduces the likelihood of unauthorized access and enhances the overall security of your smart home.
Below are the step-by-step instructions on how to enable Two-Factor Authentication (2FA) on your smartwatch:
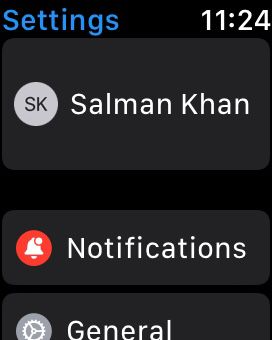
- Open the settings menu on your smartwatch and click on the option labeling as Your Name.
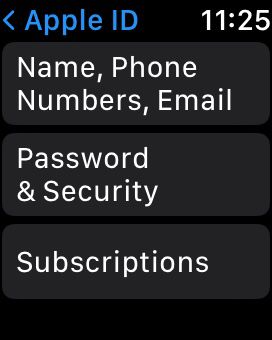
- Within the security settings, click on the Password and Security option.
- Click on the Two-Factor Authentication option and tap on it to enable 2FA.
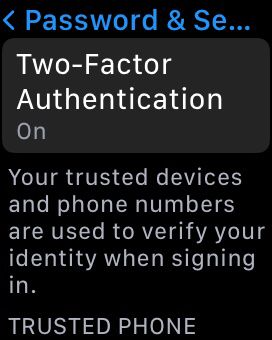
- During the setup process, the system will prompt you to enter your trusted phone number for 2FA verification.
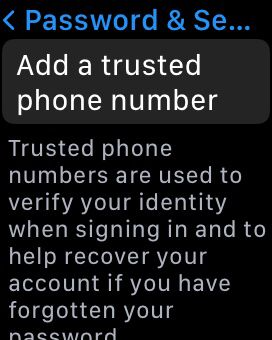
- Enter your phone number.
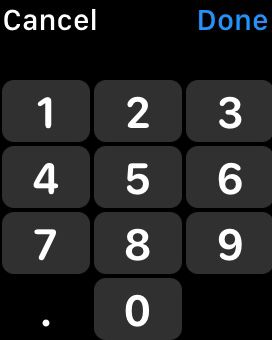
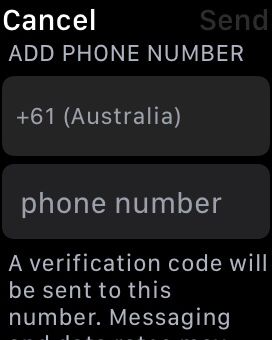
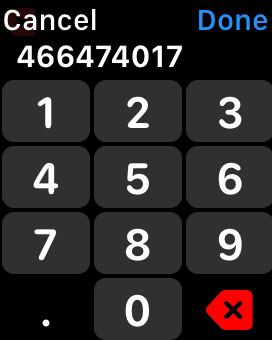
- Once you’ve completed the setup process, a confirmation message/call will indicate that 2FA has been successfully enabled on your smartwatch.
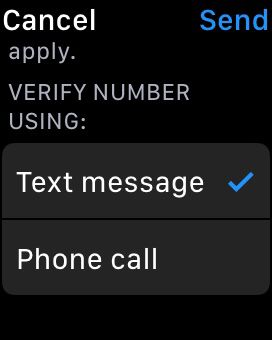
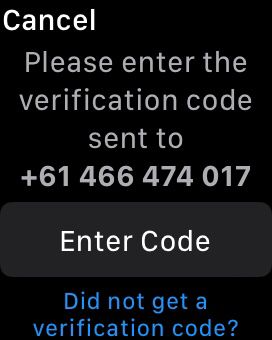
By following these steps, you can enable Two-Factor Authentication on your smartwatch, add an extra layer of security to your account and protect it from unauthorized access.
- Keep device software up-to-date
Smart home device manufacturers regularly release software updates to address security vulnerabilities and improve the functionality of their products. It’s essential to keep your devices’ software up-to-date by regularly checking for and applying these updates.
Hackers can exploit known security flaws in outdated software. It’s important to stay current with firmware updates to minimize the risk of potential attacks. By doing so, you equip your devices with the latest security patches.
Below are the step-by-step instructions on how to update the software on your smartwatch:
- Make sure to connect your smartwatch to a stable Wi-Fi network or pair it with a smartphone that has an active internet connection.
- On your smartwatch’s home screen, access the settings menu.
- Look for the About section in the settings menu and select it. This will take you to the system information screen.
- Within the system information screen, search for the Software Update option.
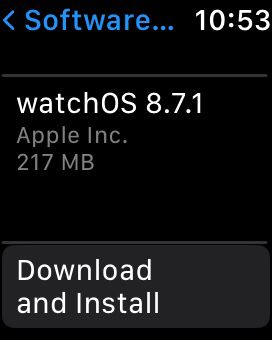
- Your smartwatch will now check for available updates. If the system detects an update, it will display a notification or prompt on the screen. Follow the on-screen instructions to download and install the software update.
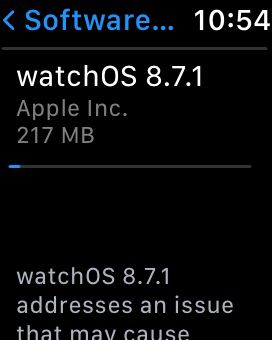
- Once the update is successfully installed, your smartwatch will restart to finalize the software update
- After the restart, go back to the settings menu and verify that your smartwatch is now running the latest software version
By following these steps, you can easily update the software on your smartwatch, ensuring that you have the latest features, bug fixes, and security patches for an optimal user experience.
- Secure your Wi-Fi network
Use a strong password for your Wi-Fi network and enable WPA2 or WPA3 encryption to prevent unauthorized access. Rename your Wi-Fi network to something not revealing your personal information or the router you’re using.
Avoid connecting to your smart home devices or accessing them remotely through public Wi-Fi networks, as they can be compromised. Utilizing a secure and private network significantly reduces the risk of unauthorized access to your smart home devices.
- Disable unused features
Smart home devices often have many features, but not all may be necessary or useful. Disabling unused features can reduce the attack surface and improve the security of your device. For example, if you don’t use the voice control feature on your smart speaker, disable it.
Below are the step-by-step instructions on how to disable Siri on your smartwatch:
- On your smartwatch’s home screen, access the settings menu.

- Look for the Siri option in the settings menu and select it. This will take you to the Siri settings screen.

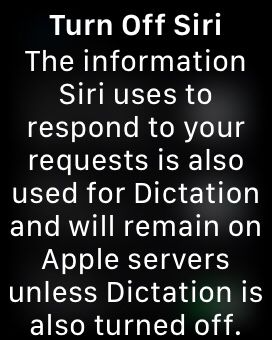
- Within the Siri settings screen, you will find the option to disable Siri. Toggle the switch to the Off position to disable Siri on your smartwatch.
- A confirmation prompt may appear, asking if you want to disable Siri. Select Turn Off Siri.
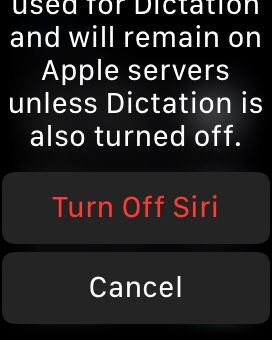
- After disabling Siri, you may also want to customize or turn off any other related settings, such as Hey Siri voice activation or Siri suggestions.
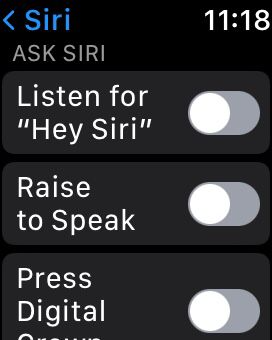
- After you have made the necessary changes, exit the settings menu to disable Siri on your smartwatch.
By following these steps, you can easily disable Siri on your smartwatch, allowing you to customize your voice assistant preferences and use alternative methods for interacting with your device.
- Install security software
To provide an extra layer of defense, consider investing in a reputable security solution specifically designed for smart home environments. Firewalls and antivirus software actively detect and block potential threats, effectively mitigating malicious activities.
These solutions often provide real-time monitoring, anomaly detection, and secure network traffic management, bolstering the overall security of your smart home ecosystem.
- Data tracking and monitoring
Data tracking and monitoring are critical for maintaining security in smart home devices. By closely analyzing device usage patterns and sensor data, you can detect potential security breaches and take immediate action. Real-time monitoring helps identify anomalies and prevent unauthorized access or data compromise.
Always review the privacy policies associated with smart home devices – by carefully examining these terms, you can check whether the device’s data collection, storage and sharing align with your preferences and expectations.
Below are the step-by-step instructions on how to turn on the App Privacy Report on your smartwatch:
- On your smartwatch’s home screen, access the settings menu.
- Look for the Privacy section in the settings menu and select it. This will take you to the privacy settings screen.

- Within the privacy settings, tap on the App Privacy Report option.


- You will see the option to enable the App Privacy Report. Toggle the switch to the On position to activate it.

- Once enabled, the App Privacy Report will provide you with detailed insights into the data usage and privacy practices of your installed apps.
- Within the App Privacy Report, you can review the information and permissions accessed by your installed apps, helping you make informed decisions about your data privacy.
By following these steps, you can easily turn on the App Privacy Report on your smartwatch, allowing you to stay informed about the privacy practices of your installed apps and make privacy-conscious choices.
- Preventing data logging
Data logging in smart home devices can have both positive and negative consequences. While it enables personalized experiences and efficient automation, improper logging practices can compromise your privacy and lead to data breaches. Robust security measures such as encryption, secure storage, and user consent are essential to mitigate these risks and enhance overall security in smart home environments.
- Use a VPN
A VPN encrypts your internet connection, adding an extra layer of security and making it more difficult for hackers to intercept your data. Get Private Internet Access and improve your smart home security.
PIA offers a wide network of servers across the world, allowing you to access geographically restricted content and bypass censorship. It also prioritizes your privacy by implementing a strict no-logs policy, ensuring that your online activities aren’t stored or monitored.
Furthermore, PIA employs advanced encryption protocols to safeguard your data, while offering fast and reliable connection speeds. Enjoy a secure and private online experience, protecting your sensitive information and maintaining anonymity while browsing the internet.
- Set up a VPN on your router
Setting up a VPN on your router ensures all devices connected to your network benefit from the added security of a VPN. This is particularly useful for smart home devices that do not support VPNs directly.
Here are five advantages of setting up PIA on router:
- Enhanced connection security: By installing PIA on your router, you safeguard your connection from its origin point.
- Constant VPN protection: Benefit from around-the-clock VPN protection on all devices within your household.
- Convenient control: Easily manage PIA using a user-friendly app or configure it once and let it operate in the background.
- Streamlined device connectivity: Connect numerous devices in your home using just one of your unlimited device connections.
- Comprehensive protection: Safeguard gaming consoles, Internet of Things (IoT) devices, and other technologies lacking built-in VPN support.
- Prevent Data Leaks: Ensure no data leakage occurs with a network-wide Kill Switch feature.
Using a VPN Router in 3 Simple Steps
Getting started with a VPN router is a straightforward process. Just adhere to the following three steps to set up your device and connect to secure servers, allowing you to change your virtual location to any part of the world from the comfort of your home.
Step 1: Register for Private Internet Access (PIA)
Begin by signing up for a Private Internet Access (PIA) account. This will grant you access to their VPN services.
Step 2: Purchase a Router Compatible with VPN
Next, acquire a router that’s compatible with VPN functionality. This will ensure seamless integration with PIA and enable secure connections.
Step 3: Install PIA and Establish a Server Connection
Set up PIA VPN on your router. The procedure varies slightly based on your router model. Follow these steps to secure your entire network with PIA VPN at the source.
- Subscribe to PIA.
- Verify router compatibility.
- Configure PIA on your router.
- Connect to a server and stay safe online.
By implementing these comprehensive security measures, you can enjoy the convenience of a connected smart home without compromising your online safety.
Smart Home Privacy – Best Practices
Yes, you can improve the privacy of your smart home by implementing several best practices and taking proactive measures.
The following table presents essential strategies to safeguard your privacy, from secure communication protocols to transparent privacy policies.
| Privacy issues | Consequences | Control measures |
| Data Collection | Potential misuse of personal information | Review privacy policies, limit data sharing, opt for devices with local storage, and minimize data collection |
| Hacking |
Unauthorized access and control | Implement strong password, enable 2FA, update firmware, and secure networks |
| Firewall |
BLack of network protection | Install and configure a robust firewall to monitor and control incoming and outgoing traffic |
| Strong passwords |
Increased vulnerability to attacks | Use unique, complex passwords and consider using password management tools for enhanced security |
| Cyber attacks |
Breach of sensitive data | Keep devices updated, install security patches, and use antivirus software to detect and prevent attacks |
| Lack of encryption |
Potential exposure of sensitive data in transit | Ensure devices use strong encryption protocols, secure communication channels, and prioritize end-to-end encryption |
| Inadequate privacy settings |
Compromised privacy settings | Regularly audit device permissions, disable unused features, and carefully review privacy settings |
Centrally Managed Smart Homes: Balancing Convenience and Security
If you’ve got a centrally managed smart home, you control all your smart devices through a single platform or app provided by your ISP or a third-party service provider. Although this allows for a unified and easy-to-use interface for managing your smart home, it has some potential drawbacks.
Entrusting your data to a third-party provider can expose you to more risk, i.e. you’ll now have to stay updated on any data breaches or evidence of misuse from that company as well.
Since a third party operates the platform, you may need more control over the security settings of your smart devices, otherwise they might become vulnerable to hacking and other security threats.
On the other hand, managing your smart home locally with a platform like Home Assistant can simplify the experience and give you more control – you’re not dependent on a single provider, which allows you to choose the devices you want and switch to a different platform if needed. You also have complete control over the security settings of your devices, reducing the risk of data breaches and hacking.
Final Thoughts on Strengthening Your Home Security System
Securing your smart home is essential if you don’t want your personal information to fall in the hands of cybercriminals. By following the steps outlined in this article, you can significantly enhance the security of your smart home.
Furthermore, using a VPN gives you an additional layer of protection, providing encryption for your internet traffic and preventing unauthorized access to your network. Use PIA and protect all devices on your network by configuring it on your router.
PIA VPN offers robust security features, easy-to-use applications, and a strong commitment to protecting privacy. Don’t wait for a security breach – it’s going to be too late by then – secure your smart home with PIA VPN right now.
FAQ
Smart homes can be a security risk if the devices are not properly configured. The interconnected nature of smart home devices and their reliance on the internet makes them potential targets for hackers.
You can minimize the risk with proper privacy measures and security protocols.
Smart home security can be vulnerable to malicious parties, but implementing cybersecurity best practices, such as using unique passwords, enabling two-factor authentication, and keeping firmware up to date, can help mitigate the risk and enhance overall security.
To secure your smart home:
– Use strong, unique passwords
– Enable two-factor authentication
– Update device firmware regularly
– Secure your home Wi-Fi network with encryption and a strong password
– Consider network segmentation, be cautious with permissions and data sharing, and
stay informed about cybersecurity best practices.
Configuring PIA VPN on your router can improve security by encrypting traffic and masking your IP. It shields your smart home devices from prying eyes, making it more difficult for hackers or malicious actors to intercept or exploit your network traffic.
That said, choosing a reputable VPN provider and configuring it correctly is important to ensure optimal security and privacy for your smart home ecosystem.
