Another day, another breach: At what point does storing passwords in plaintext become criminally negligent?

The third largest breach ever in Finland happened yesterday. Passwords were stored in plaintext. At T-Mobile Austria, they explain that of course they store the password in plaintext, but they have so good security so it’s nothing to worry about. At what point does this become criminally negligent?
News of the Finnish breach (Google Translate) arrived yesterday, and while there isn’t a lot of details, we learn two important things: the leak was relatively big (the third largest in Finland), and cleartext passwords with usernames leaked, because they had hundreds of thousands of passwords stored in cleartext.
…and they had passwords stored in cleartext.
This is so bad security, it should not exist anywhere, period. It should not even be taught in a coding class as an intermediate step on the way to how to do it the right way.
You don’t store passwords in cleartext because of two reasons combined:
1) You don’t need to store a password in cleartext to check it against a new input of the same password. You use something called a salted hash of the password, which means that you scramble it in a one-way method that it can’t be unscrambled, but the scrambled result can be compared to a second scramble with the same method of the typed password (and if they match, it was the same password to begin with).
2) The leak of a plaintext password can be catastrophic for the user concerned, and the possibility of an external or internal breach must always be taken into account. No matter how small the possibility, if the consequences are big enough, we need to take precautions.
(Even if a given user uses different passwords on every platform, those passwords can be derived from the platform name in a way that a plaintext leak from one platform will make it significantly easier for an adversary to guess the password of any other platform. And most users re-use passwords quite liberally, even if they shouldn’t.)
This is why you don’t store passwords in plaintext. You don’t ever do this. This is a sign of such sloppy security attitude, it’s a complete dealbreaker for me for any company I do business with — for if they’re allowing such sloppy (bad!) security to exist in one place, their attitude will allow it to exist in other places too. It’s not just sloppy and ignorant, it’s dangerous.
This is why it’s possibly infuriating to see an exchange like this on Twitter, this time with T-Mobile Austria, but the probability is overwhelming that several Fortune 500 companies are guilty of this negligence:
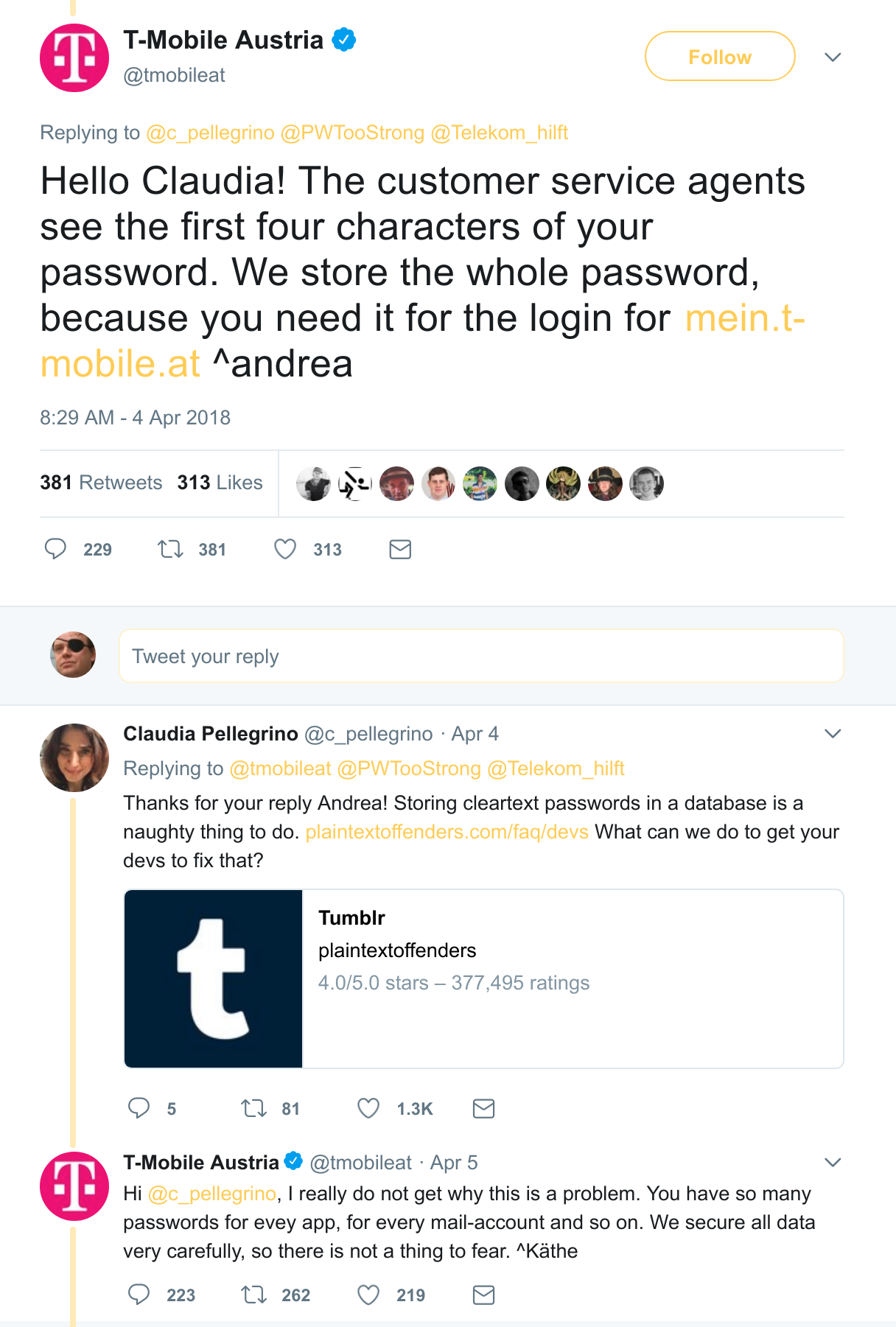
This is getting to the point of the SOPA debate:
It’s no longer okay to not understand the very basics of how the Internet works.
It’s no longer okay to say “yes, we store the passwords in plaintext, but don’t worry, we have good security”, when you just told me your security is horrifyingly deficient, right there.
It’s no longer okay to pretend it was “just an unfortunate random event” when plaintext passwords and similar details leak, when it’s the first things you learn about computer security.
At what point is a plaintext password leak simply considered criminally negligent, merely for the sloppy and ignorant engineering that made it possible in the first place?
Privacy remains your own responsibility.
Comments are closed.

https://xkcd.com/792/ in poster size on my flat’s door ;-)