Hacking the World – Part 4: The Cost and Future of Hacking (Plus: Safety Tips)

We finish our four-part Hacking the World series with two key questions: how much does hacking cost per year and what’s coming next? It’s not a surprise that hacks cost money. We’ll cover some of the biggest, costliest data breaches, how much money is lost to hacking, and take a peek at what the cybersecurity future holds. To round up your read, we’ve also compiled a few basic cybersecurity tips to help keep you safe online.
Before looking ahead, a reminder that we’ve covered the basics, what’s being hacked (with Covid updates), and the who and where of hacking. For a refresher of key hacking terms and definitions, read our helpful cybersecurity glossary from Part 1.
Jump to a section below, or read on:
The Cost of Hacking
The Future of Hacking
Safety Tips to Prevent Cyberattacks
The Bottom Line
The Cost of a Breach
Data breaches cost time and money. Lots of it.
In addition to covering the immediate damages of a cyberattack, companies must pay out compensation and data protection fines, all while investing in cybersecurity systems. The downtime and consequently lost business of a breach add substantial costs too.
The Growing Cost of Hacking

The monetary damages of cybercrime are already sky-high and they’re only heading up. In 2015, hacking attacks incurred damages upwards of $3 trillion. By 2025, cybercrime is expected to cost us a whopping $10.5 trillion per year.
More and more businesses are turning to digital solutions. However, as companies pursue fresh web-based systems and cybersecurity catch-ups, hackers also improve the complexity and frequency of their attacks.
Top 10 Costliest Breaches
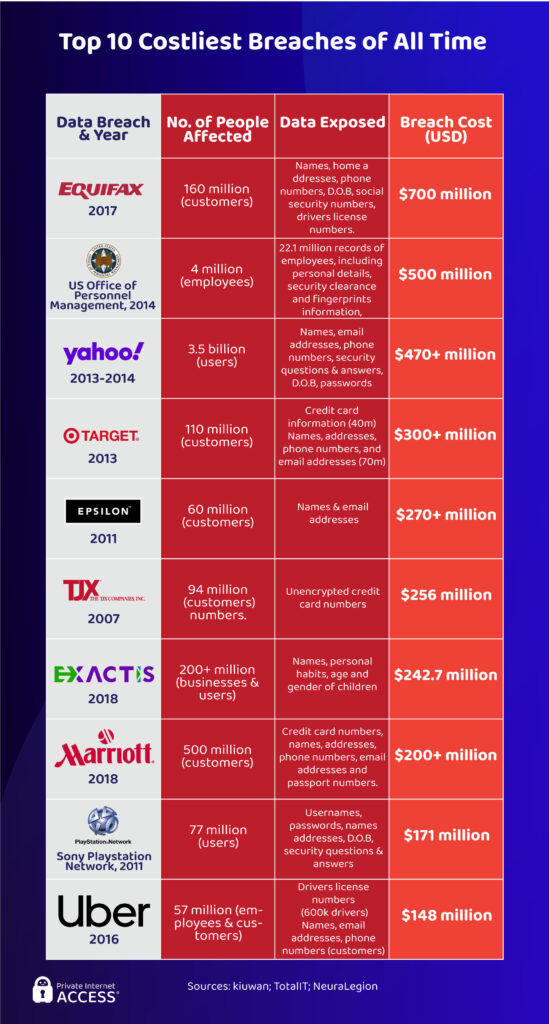
To start, let’s take a look at some of the most financially devastating breaches of all time.
The costliest breach on the list is Equifax, with reported damages of $700 million. The breach affected around 160 million customers, revealing their names, addresses, phone numbers, social security numbers, and other personally identifiable information (PII).
That said, the actual cost of hacking damages can be somewhat of a gray area as they’re not always completely disclosed or calculable. Experts predict that Epilson’s data breach damages could have reached a whopping $4 billion.
In the same vein, despite the fact that Marriott reported only $200 million in damages, the franchise’s losses were likely closer to $1 billion if we consider the potential loss of future business.
A (dis)honorable mention has to go to the US Veterans Administration, which leaked the data of 26.5 million US veterans. The costs related to the incident are thought to range anywhere from $100 million to $500 million.
How Much Does a Data Breach Cost?

Data breaches have maintained a fairly consistent cost since 2014. On average, breaches cost companies $4.24 million per leak in 2021. That’s a significant increase from the average of $3.86 in 2020. Meanwhile, the average price per stolen record was $161 in 2021, which is $11 more than in the year prior.
Breaches Have Longtail Costs

Organizations are not just dealing with the immediate economic fallout of breaches. Numerous factors at play mean costs can span over more than two years.
Immediate damages, such as the costs of lost data and system downtime, are usually paid in the first year of a breach. This is usually the most expensive part of managing a data breach as it makes for over half of total expenses.
But while immediate damages are the costliest, many businesses feel certain impacts long after the hack occured. Reputational damages and lost customers in particular affect a company well into the third year after an attack. That’s why 16% of total data breach costs come after 2 years — sometimes even putting companies out of business.
The Cost of Lost Business

Lost business accounts for 40% of the average company’s breach-related expenses ($1.52m). This includes incurred losses from business disruptions, system downtime, and reputational damages.
Detecting and investigating data leaks costs around 29% ($1.11m) of overall costs and post-incident response, such as data protection fines and legal damages, accounts for 25.6% ($0.99m) of data breach costs.
Detecting and investigating data leaks makes around 29% ($1.11m) of overall costs. Post-incident response, such as data protection fines and legal damages, is almost as expensive as it accounts for 25.6% ($0.99m) of data breach-related fees.
Data breach notification involves liaising with regulators, data subjects, and third parties. This process is still an important part of a data breach response, but it’s not as costly, coming at just $240,000 per breach (6.2% of overall costs).
The high costs of detection and escalation alongside lost business indicate that time is money: acting fast often reduces monetary damages. In fact, IBM found that breach lifecycles under 200 days cost businesses, on average, $1 million less than their longer counterparts. For many companies, $1 million can be a make or break difference.
Malicious PII is the Costliest Data

Data breaches cost more money when bad actors are to blame. IBM found that malicious breaches cost target organizations $1 million more than your average data breach. Nation-state attackers were the costliest actors and stolen credentials were the costliest root cause.
There are 3 types of hacking, and not all of them cause damages. White hat hackers are the good guys. They use ethical methods to break into organizations that hire them — and with that find existing weak points of entry for the malicious actors, known as black hat hackers. The latter always act with an evil intent, as their aim is to cause havoc and steal vulnerable data.
Then, there’s a group of hackers who are in the gray area. They don’t want to break into anyone’s network to leak files, but they also don’t help businesses without asking for something in return. Gray hat hackers can utilize malicious software to identify weak points in a company’s cyber defense; then, they reach out to them to report the vulnerabilities and ask for compensation. If they don’t receive monetary reward, they may choose to steal said data even though they’re not malicious by nature.
The cost of hacking is higher when bad actors are to blame. IBM found that malicious leaks cost target organizations $1 million more than an average data breach. The research showed that nation-state attackers caused the biggest financial losses, and stolen credentials were the most expensive root cause.
Malicious breaches are more damaging for companies because they are targeted — tailored to specifically exploit an organization’s systems, processes, or personnel. This leads to bigger breaches, more sensitive data leaked, higher subsequent levels of cybercrime, and more expensive fines or lawsuits.
Additionally, malicious breaches take an average of 315 days to identify and contain. That’s significantly longer than other root causes, as system glitches usually require 244 days and human error leaks need only 239 days to fix. Among other things, the time difference increases the incurred costs due to longer system downtime.
Breach Cost: Expensive Industries
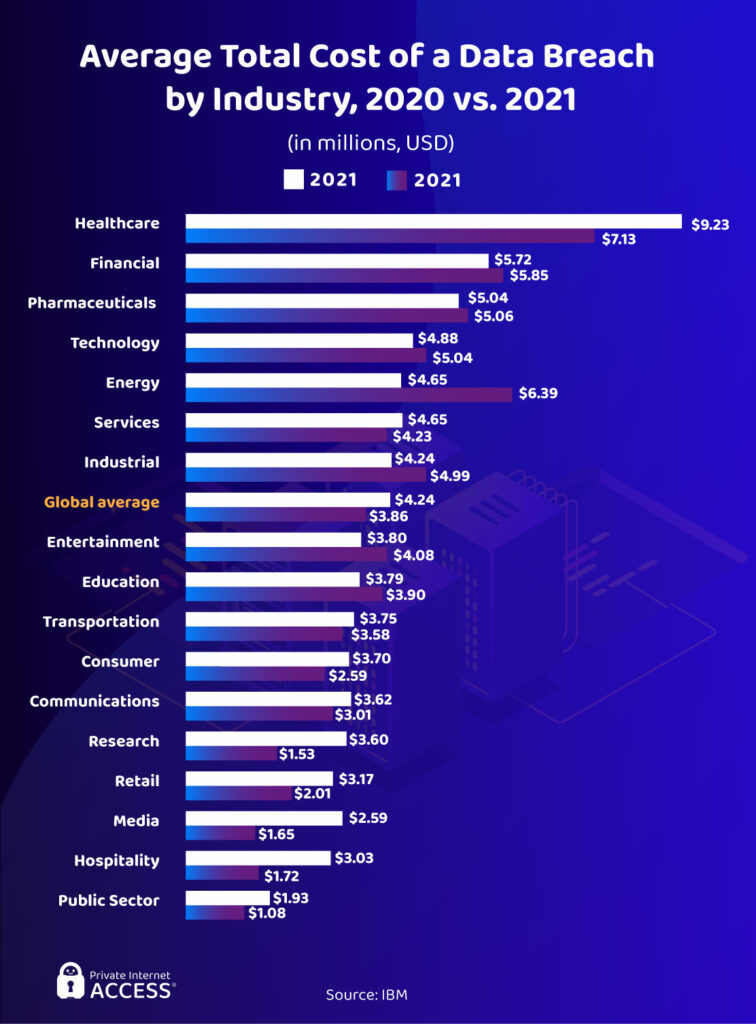
The healthcare industry suffers the costliest breaches out of any sector, averaging at $7.13 million in 2020 (nearly twice the global average). Hospitals, pharmacies, and other medical organizations seem to have a poor level of security — which is surprising considering their high-value customer records. That’s why malicious actors regularly target the health industry, causing big data breaches and significant damages both for the organization itself and the victims.
The energy sector ($6.29 million) and the financial sector ($5.85 million) also face big damages from breaches. At $18.3 million per company surveyed, Accenture notes that financial companies take the biggest economic hit from all types of cybercrime.
Media, hospitality, and research companies are less regulated than the aforementioned industries. They often still hold vulnerable customer data, but at lower quantities than finance of healthcare sectors. Public sector businesses are usually able to retain their customers after a breach, so they don’t suffer from high breach costs.
Mega Breaches: An Expensive Trend

Mega breaches are attacks that expose at least 1 million records, costing organizations higher sums of money. The price of a mega breach has been on an upward trend too, meaning it’s more likely to cause more damages in the future.
Depending on the size of a mega breach, companies have to fork out a significant amount of money to cover damages. Mega attacks exposing 50+ million records cost an average of $392 million in 2020. That’s a 12% growth since 2018.
The cost increase is linked directly to the rise of big data, personalization, and data analytics, which means big corporations are collecting more of your data than ever before. Data collection on such a scale requires huge servers to store all of your credentials and personal information. Hackers will, inevitably, target big data stores given their bounty of valuable information.
The Biggest GDPR Fines

The EU’s General Data Protection Regulation (GDPR) laws are recognized as the toughest data protection laws in the world. It dishes out some of the biggest fines, which adds significant costs to hacking damages, and these fines are handed out to companies deemed to have mishandled the data of EU citizens. The GDPR directly affects businesses in the EU, but also any business outside of the GDPR jurisdiction if they want to work with EU citizens.
The max fine for a GDPR breach is €20 million (~$21 million) or 4% of the company’s annual turnover (whichever is greater). As of today, GDPR fines may reach even €50 million (~$52.5 million), but it’s still not the only related cost since 88% companies have to spend over $1 million when trying to meet its security standards.
Companies and GDPR Compliance

Where other privacy regulations focus on sanctions and punishments for poor data protection, the General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) are more concerned with compliance. Both regulations demand a long list of specific data-handling standards and practices. The GDPR came into effect in 2018 and the CCPA, which is inspired by the former, covers entities in California and was initiated in 2020.
Organizations must pay to reach compliance, and failure to do so could cost businesses in more ways than one. The DLAPiper research shows that a vast majority of companies are either fully, very, or moderately compliant with the new legislation, especially when it comes to CCPA. Only 1% of organizations turned out to not follow either at all.
The Cost of Compliance: GDPR

The GDPR requires businesses to spend significant sums of money to introduce and maintain satisfactory data-handling practices, systems, and technologies. On average, companies are spending well over $1 million to reach compliance with the regulations. In the United States alone, 40% of businesses are going above and beyond to secure user data with an outlay of $10+ million on GDPR.
The Cost of Compliance: CCPA

California state-sanctioned research outlined the estimated average cost of CCPA compliance based on the size of a company. The study assumes that around 75% of businesses based in California are subject to the local data protection legislation.
Collectively, Californian businesses will spend $55 billion to reach initial compliance with the CCPA. That’s equal to roughly 1.8% of the region’s Gross State Product in 2018. The research shows that even companies with less than 20 employees have to pay an average of $50,000. That cost drastically increases the bigger a business gets, finally reaching $2,000,000 for organizations with over 500 employees.
The future looks a lot more expensive for Californian businesses. The direct compliance costs over the next decade will be significant, collectively reaching anywhere from $467 million to $16.5 billion, according to the report.
The Cost of Compliance Failures

Compliance failure describes any case of negligence when it comes to securing customer data, which organizations must shoulder the blame for. That’s because compliance failure often leads to bigger, more impactful data breaches, larger fines, and additional sanctions.
Compliance failures cost businesses a lot of money, further increasing the average cost of a data breach. In fact, this was the biggest cost amplifying factor in IBM’s study as even low level costs averaged at $3.35 million. However, high level costs reach as high as $5.65 million!
Cybersecurity Spending Per Sector

Across all sectors, the average revenue companies spent on cybersecurity increased from 0.34% in 2019 to 0.48% in 2020. That equates to 10.9% of each business’ IT budget, which rose by 0.8% since 2019. In money terms, that’s $2,691 per employee in 2020 vs. $2,337 the year prior.
According to ESG Master, 47% of organizations have planned to increase their cybersecurity spend in 2021 — and in the years to come. This upward trend comes as companies attempt to quell the intense wave of cyberattacks following the outbreak of COVID-19.
Top Cybersecurity Investments

Total cybersecurity spending surpassed $123 billion in 2020. Embroker research shows that organizations are primarily investing in infrastructure protection ($17.5 million), network security equipment ($11.7 million), and identity access management ($10.4 million).
There are, of course, companies that neglect cybersecurity spending. However, these are usually smaller businesses that don’t have the budget to account for online protection. So, though it’s very concerning, it’s not surprising that 54% of small companies don’t have a cybersecurity response plan in place. Additionally, 65% of them fail to react to hacking incidents at all, causing worse damages than many large corporations experience.
Data suggests that companies of all sizes need to invest more in risk assessments, too. A meager 57% of businesses carried out a data security risk assessment in 2020.
Cyber Insurance Reduces Costs

Cyber insurance is a developing field that aims to help businesses cover the expenses associated with data breaches. It basically works like any other insurance you can buy, with payable monthly fees and a guarantee that you’ll receive help should you experience a cyberattack.
Primarily, cyber insurance claims compensate for consulting and legal costs. Restitution payments are paid for 36% of businesses, and regulatory fines are covered for roughly one-third of organizations.
The Cybersecurity Gap: SMBs Pay the Price With Data

There is a clear gap between the cybersecurity posture of security leaders and non-leaders. Leaders are often bigger businesses with more resources, while small companies usually fall into the latter category.
What’s more, leaders can mitigate the impact of cyberattacks far better than non-leaders, reducing the amount of data loss and subsequent breach costs. This comes despite facing a higher volume of cyberattacks.
So, how are non-leaders paying for a lack of maturity in their cybersecurity strategies? With data. Accenture’s survey revealed that 44% of non-leaders exposed 500,000 records or more in 2020. On the other hand, only 15% of cybersecurity leaders experienced the same situation that year. This shows a massive gap that needs fixing if companies want to avoid the high costs that come with cleaning up after data leaks.
Security Leadership Reduces Costs

A Chief Information Security Officer (CISO) is an executive who’s responsible for the establishment, maintenance, and management of an organization’s cybersecurity strategy. A Chief Security Officer (CSO) oversees the security of all aspects (personnel, physical assets, and data).
Executive-level security pros are integral to an organization’s cybersecurity team. In IBM’s survey, 46% of experts believe the CISO is the “most responsible” person for any data breach. That’s because a security executive can provide the leadership necessary to elevate a company’s strategy and lessen the impact of a breach.
Businesses are now beginning to recognize the importance of skilled leaders, too. According to Gartner, 40% of companies plan to have a dedicated cybersecurity committee that’s supervised by a board member by 2025. As of today though, that figure stands at only 10%.
Leaders Sustain Existing Tech

Cybersecurity leaders are allocating their security budgets tactfully, across piloting and scaling new technologies, with a focus on sustaining current security solutions.
The data suggests that great security is not just about buying up the latest tech as it becomes available. Non-leaders focus their spending on trialing new technologies. However, leaders master the basics and consolidate what they have—part of the reason these departments are so successful.
Cost Difference: Leaders vs. the Rest

Non-leaders have a high chance to save a ton of money, but they need to implement better investments and procedures in their security departments. That’s because their current security solutions are failing them, which leads to a higher chance of successful breach followed by a lackluster breach response.
We mentioned how non-leaders pay for their cybersecurity shortcomings with data. This means they experience regulatory actions more often than security leaders (19% of non-leaders vs. 13% of leaders). Non-leaders are also more likely to face fines compared to security leaders (19% of non-leaders vs. 9% of leaders).
With better data handling comes fewer fines and monetary remediations. This could result in non-leaders saving nearly $300,000 per breach simply by improving their cybersecurity. That’s a drop of over 70% from current costs of $380,000.
The Future of Hacking and Cybersecurity
Let’s explore the cybersecurity forecasts for the future. We’ll look at the predicted cost of hacking, expected threats and vulnerabilities, and the technology of tomorrow.
Cybersecurity Set for Exponential Growth

The cybersecurity market is expected to reach an eye-watering $430 billion by 2030 at its forecasted annual growth rate of 9.1%. The large increase is mainly linked with the fact that almost every company massively increased its cybersecurity spend to deal with record levels of cyber crime.
You can expect this trend to continue as we move into the digital age. Hacks will definitely increase the severity and sophistication of their attacks, causing more severe destruction. Cybersecurity Ventures predicts the cost of hacking damages could reach $6 trillion by the end of 2021. Cybersecurity teams must keep up to protect customer data — resulting in much higher budgets for all related measures.
Digital Transformation Presents Some Issues

Many organizations have accelerated their digital transformations: their adoption of new technologies, on the one hand, and development of cybersecurity processes, on the other. This has come as a result of the rise in cybercrime over the pandemic.
In IBM’s study, organizations that failed to implement any kind of digital transformation were left behind, and this increased their data breach costs by an average of 17%. That being said, 80% of organizations still aren’t able to secure their new systems quickly enough. It’s an issue that could present a multitude of entry points to hackers, despite everyone’s attempts to create a more secure online environment.
Data Breaches Will Become Less Damaging
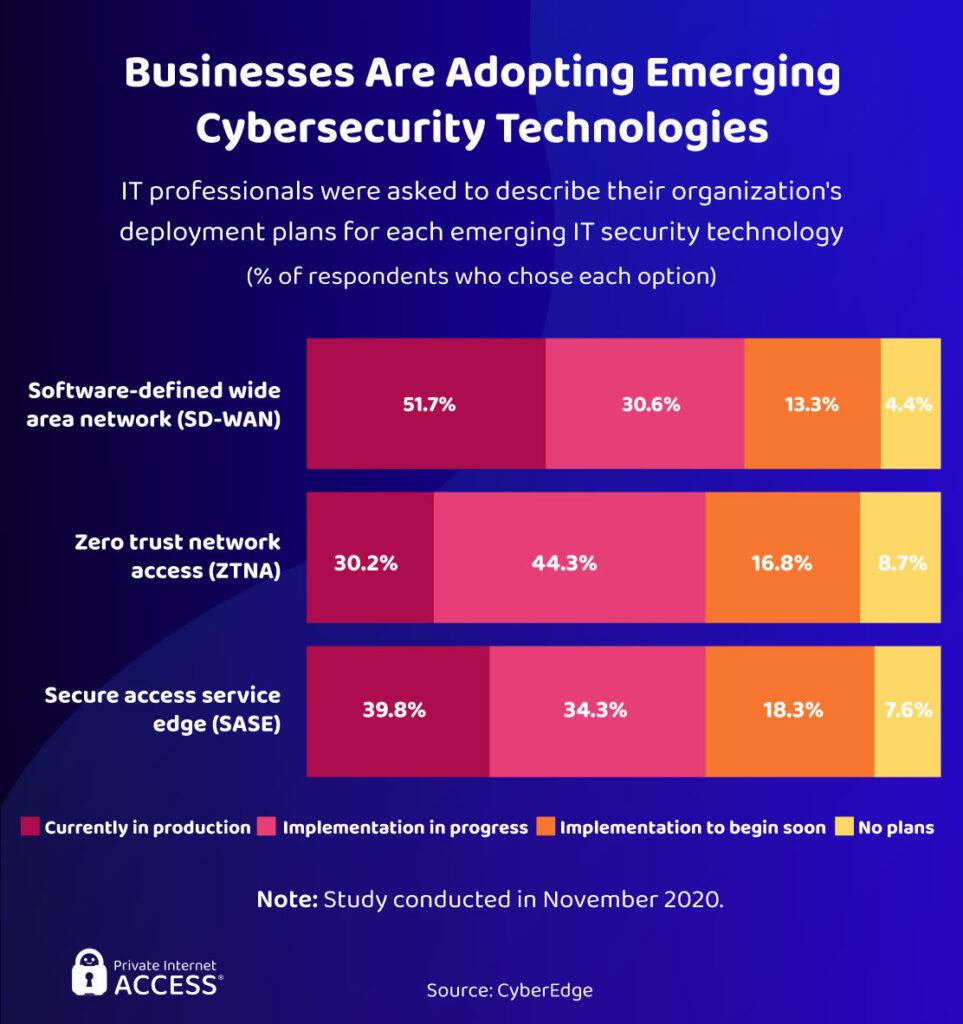
A number of emerging IT technologies (many of them utilizing Artificial Intelligence) are contributing to a general reduction in the damages caused by cyberattacks. This is expected, as cybersecurity departments become more sophisticated to counterbalance up and coming hacking attacks.
A VMware survey of Chief Information Security Officers (CISOs) found that 98% of businesses use, or plan to use, a cloud-first cybersecurity strategy. Dedicated Security Operations Centers (aka SOCs) are predicted to become more common as well, growing at 28.6% every year until 2025.
To be clear, these technologies are already playing their part. Despite record levels of cyber activity, 66% fewer US citizens were impacted by data breaches in 2020 than in 2019. This gives everyone an optimistic outlook for the future.
AI & Automation Is the Future
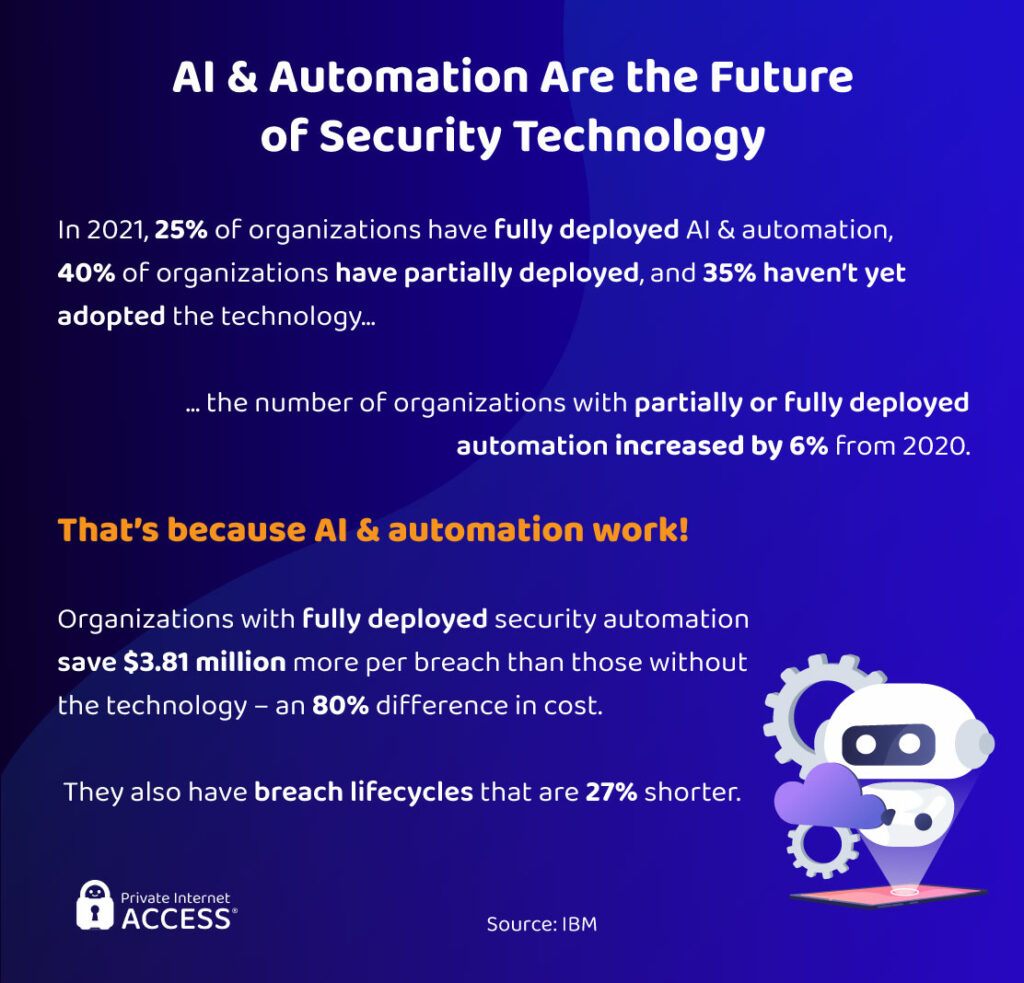
Artificial Intelligence, automation, and machine learning are the cream of emerging cybersecurity technologies. These systems vastly improve an organization’s ability to detect and respond to a data breach through the use of AI, and they lower the cost of hacking responses.
Research shows that organizations that fully deployed their security automation spent $3.81 million less per breach than other companies. That’s an 80% cost difference!
According to Nominet, 75% of CISO’s believe that AI will reduce the amount of stress they experience at work. The reason behind it is simple: AI technologies can detect new threats and shift with changing hacking trends unlike any human. That’s an important trait given the fast-paced nature of today’s cybersecurity landscape.
Hybrid-Cloud Will Dominate

The hybrid cloud is made up of physical on-premises infrastructure and public cloud services. Hybrid cloud combines the security of internal storage solutions with the ease and data visibility that comes with cloud storage.
That’s why more and more organizations are converting to this method and seeing results. IBM found that hybrid cloud saves organizations $1.2 million per breach compared to public-cloud-only companies, and $940,000 per breach compared to businesses using private cloud. These findings make it clear why 32.7% of companies plan to implement the hybrid storage solution within the next year or two.
Companies Will Scale Encryption
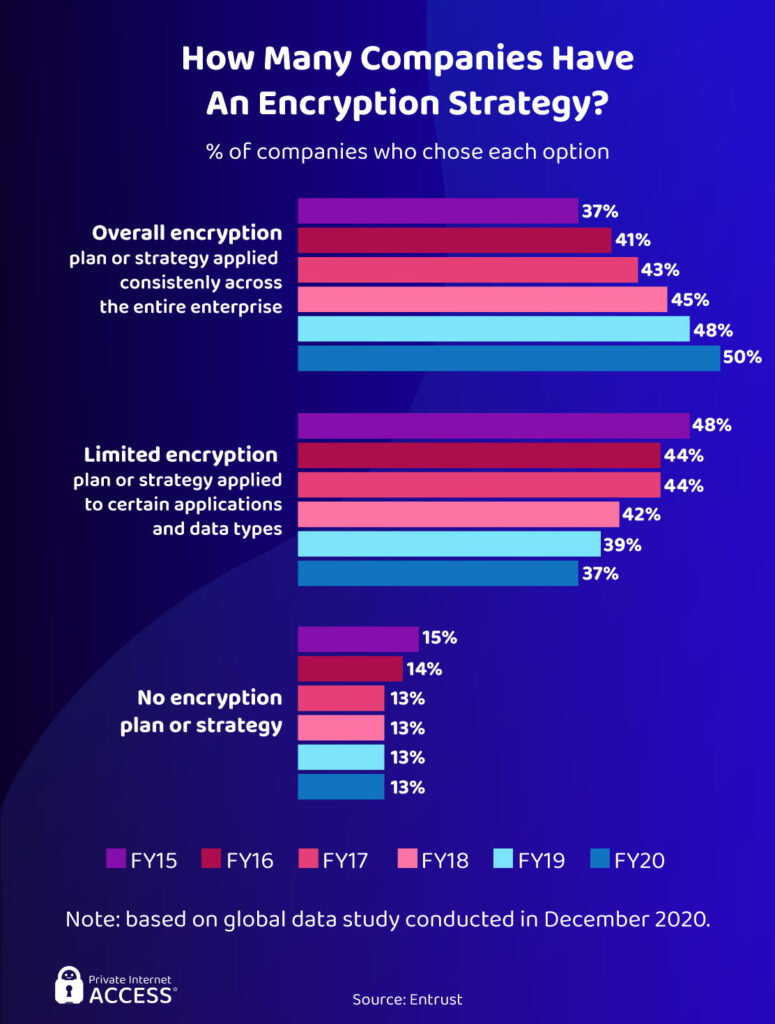
Encryption should be an essential part of an organization’s data security strategy. But even though many businesses have adopted it over the last few years, only 50% of companies consistently use encryption across all of their applications.
IBM’s study found that encryption was the third biggest cost mitigating factor in a data breach. Companies with high standard encryption pay, on average, $1.25 million less per breach than those with low standard encryption.
The future will see every business encrypt its data consistently. Why? Because encryption works. By making data unreadable to hackers, encryption reduces the impact of a data breach as stolen credentials won’t be worth anything. It also makes you less likely to become a victim to scams or identity theft as bad actors won’t be able to decipher your details.
How Does Future Tech Rank?

Cybersecurity leaders ranked prevalent and emerging security technologies based on each option’s ability to provide specific benefits.
SOAR ranked highest for helping businesses detect threats while reducing risk and subsequent costs. That’s because the technology covers all aspects of security, from detection, management and response, to security automation.
AI also ranked well for mitigating breach impact and providing a successful response, especially considering that new technologies are overwhelmingly effective. 86% of security leaders say that the latest cybersecurity tools expand the scope of their organization’s cybersecurity coverage.
Is Security Technology Spending Unsustainable?
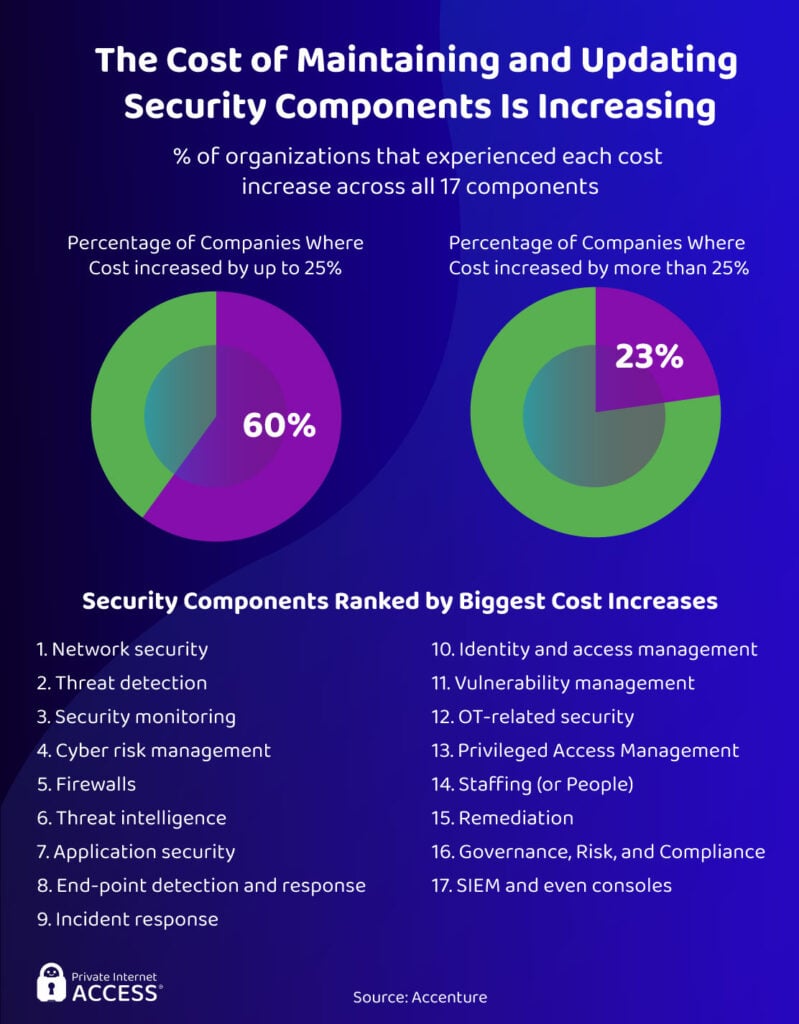
At its current rate, the vast sums of money companies spend on emerging cybersecurity technologies, tools, and systems aren’t sustainable. 60% of organizations have experienced a cost increase of 25% or more across all 17 components, such as firewalls, incident response, threat detection, and vulnerability management. Another 23% of businesses have seen more than a 25% increase in costs.
New technologies can sometimes fail organizations that are struggling to stay ahead of the curve. Accenture reveals that 69% of businesses find that outpacing hackers is a constant fight with an unsustainable financial outlay. This is particularly true for companies that aren’t well established on the market as they don’t have the budget to stay in the cybersecurity race.
Future Threats

According to research, ransomware and DDoS attacks will continue to rise in popularity among hackers as time progresses. In fact, ransomware already is the fastest growing type of cybercrime, with one ransomware attack occuring every 11 seconds in 2021.
When it comes to future targets, Experian predicts that cloud vendors will be the main victims of cyberattacks. Biometric scanners could also be a valuable source of data for cybercriminals moving forward.
IoT could become an even bigger problem area, since over 40 billion IoT devices are expected to be connected to the internet by 2025. Given IoT’s well-documented vulnerabilities, hackers will likely continue to exploit these devices for as long as they can.
Three Future Hacks and Vulnerabilities

There are several prominent areas of concern as we look towards the future of hacking.
As business ecosystems are constantly expanding in size and complexity, they will see a continued rise in cyberattacks. Supply chains and digital ecosystems create an increased attack surface, which makes life more difficult for CISO’s. According to Accenture, 83% of organizations believe they need to secure entire ecosystems, not just their own company, to create an effective protective barrier against hackers.
Businesses are becoming more interdependent as they share popular supply chains, pervading across multiple industries. Large-scale networks of services, applications and devices can therefore be hyperconnected. Hyperconnectivity means an increased likelihood of an attack that exploits multiple businesses at once. This could be a hack that targets loads of IoT devices, like smart TVs, or every business that uses a certain web service.
Finally, critical infrastructure attacks are becoming more prevalent. We’ve seen several nation-state led attacks on US infrastructure this year alone. Critical industries are shockingly vulnerable too. Four-in-ten ICS systems, which are used in manufacturing and utility companies, are susceptible to attack. Expect cybercriminals, nation-states, and even cyberterrorists to exploit them in the future.
Safety Tips for Preventing Cyberattacks
Install Cybersecurity Software
If you haven’t done it already, download an antivirus and antimalware software on your devices. There are no excuses for not doing this as there are plenty of free options and most of them include protection for various types of malware, viruses, Trojans, and ransomware.
You should get a VPN too. VPNs encrypt your web traffic to establish a secure connection to the internet. This makes for safer web browsing and file sharing as it anonymises your traffic, making it invisible to spying parties.
Update Device Software
Any devices you use regularly, be that mobile phones, PCs, or tablets, need to be kept up to date. That’s because manufacturers use software updates as an opportunity to patch any existing vulnerabilities. Installing updates can massively reduce your chances of suffering a device hack or backdoor attack.
Download Files Only From Trusted Sources
Anything that comes from the web, such as a link, email, message, or any other source, may contain malware, so you need to be careful when you download anything on your device. Before you click on anything (especially in a seemingly safe email), make sure that it comes from a trusted domain or a person. The best way to do it is to check for spelling mistakes in URLs or email addresses as it’s usually a giveaway the message isn’t trustworthy.
Create Rock-Solid Passwords
Overly simple passwords are a big no-no. They’re super easy for cybercriminals to hack and could provide almost instant access to your sensitive data. Instead, create long passwords (8+ characters) made up of upper and lowercase letters, numbers, and symbols. You should also avoid common words or phrases since these can be hacked in a brute-force attack!
Make sure you have a different password for each of your accounts, too. That way, should one of your accounts become compromised, hackers won’t be able to authenticate themselves across any other accounts you own.
Monitor for Data Leaks
Keep tabs on the brands you use and regularly monitor the status of your data/accounts. It’s impossible to completely mitigate exposure, but a quick response is feasible. As soon as you suspect something is wrong or you hear the news a business you use suffered a breach, change your account credentials to prevent further damages.
The Bottom Line
The bottom line is: Your data is under threat. Hackers and cybercriminals are in a race to collect as much data as possible, whether they are motivated by money, political affiliations, or any of the other causes we’ve highlighted in this four-part series.
The rise in big data and the ever-growing adoption of digital technologies have facilitated a massive increase in cybercriminal activity. But fear not. While hackers enjoy their most prolific period to date, cybersecurity shows every sign of catching up. Meanwhile, implementing a few of the above-mentioned cybersecurity practices will stand you in good stead as we head into a new age.
Have you read all parts of our Hacking the World series? Catch up below to be fully versed on all things hacking:
Part 1: Hacking Basics
Part 2: What’s Being Hacked (And What Changed with Covid)
Part 3: Who & Where – The Hackers and the Hacked
