Hacking the World – Part 2: What’s Being Hacked (And What Changed with Covid)

Back in the day when hacking was still new, hackers didn’t look to gain anything from their attacks. They simply wanted to let others know they could break into a computer or system. This has significantly changed over the years as bad actors from all over the world are now focused on not only accessing, but stealing all kinds of data for a variety of reasons.
It’s a more complicated issue that requires us to take a deeper look at why hackers hack and what exactly they target — from data to devices and applications. That’s not all though. We’re also going to talk about how hacking changed during COVID-19.
Need a refresher of key hacking terms and definitions? Check out our helpful cybersecurity glossary and in-depth guide to hacking basics in Part 1: Hacking Basics of our Hacking the World series.
Jump to a section below, or read on:
Risk Data, Devices & Applications
The Covid Effect
Why Do Hackers Hack?
Hackers generally don’t commit cybercrimes if they have nothing to gain from them. So what are they after? To properly understand this, we need to look at the most common targets of hacking, like the data, devices, and applications – as well as the methods hackers use to conduct each attack.
Financial Records Are Vulnerable

Companies collect a treasure trove of sensitive customer data: names, addresses, bank details, credit card information, even medical records. This information usually lacks adequate protection that would stop hackers from breaking in. To make it worse, companies generally make the records available to all employees, which only increases the margin for human error.
This is music to the ears of your average hacker. And since 64% of financial companies hold more than 1,000 customer records, it’s no wonder these organizations have become a common target for attackers — especially during COVID-19. As employees worked hard to soften the ensuing economic turmoil, cybercriminals were busy with phishing attempts, hacking systems, and capitalizing on human errors.
Globally, the financial sector experienced a 238% increase in cyberattacks between February 2020 to April 2020. Altogether, nearly three quarters of all finance companies were affected by this in 2020 alone.
So why do hackers hack financial data? Your payment details usually hold a high value on the black market. Even if cybercriminals choose to keep your data (rather than sell it), they can use it for payment frauds, like applying for loans in your name, emptying your bank account, requesting tax refunds, and more.
Financial Data Leaks: Root Causes

According to Verizon, data breaches in the financial industry are caused mostly by external actors, like hackers. The remaining 35% is carried out by internal actors, such as employees. These attacks usually happen through exploiting web applications, miscellaneous errors, phishing and social engineering — together, these account for 81% of all financial data breaches.
Over 90% of these breaches are financially motivated. Each record can be sold or auctioned for a lot of money. However, hackers also steal this data for identity theft and payment fraud that lets them collect a significant amount of money before getting caught.
Hackers can steal your financial data in many different ways. This includes processor breaches, hacked merchants, ATMs, eCommerce sites, insider threats, malware, phishing, and point of sale hacks (i.e. online checkout portals). Successful attacks let them walk away with customer credentials (in 35% of cases) and bank details (in 32%). At the very least, hackers gain access to your PII, which is already enough data to enable multiple types of scams.
Healthcare Records Are Valuable

Healthcare records hold extremely high value on the dark web, which is why they’re often targeted by hackers. Just one record costs about $250 on the dark web — this is the highest price any data holds as the next most valuable record sells for just $5.40. This means that hackers don’t need to break into the whole database to earn a substantial amount of money.
The high price stems from the nature of stolen data. Medical records feature a long list of unchangeable customer PII: names, dates of birth, social security numbers, as well as medical and employment history. This information allows bad actors to carry on their attacks for several years with the same details, as opposed to records like payment card information which usually lose their value after a single fraud attempt.
Healthcare Record Exposure: Root Causes

Cyberattack incidents caused 67% of healthcare breaches reported to the OCR in 2020. Cyberattacks were also responsible for 92% of breached records in general.
This is a common issue that only seems to be getting worse. Verizon notes that healthcare data breaches increased by 58% in 2020, when 30 million records were exposed in published OCR breaches alone. The number is set to increase if companies don’t take appropriate measures.
How are hackers stealing medical records? Tenable research shows that ransomware is the biggest threat to medical data. The next prevalent method of choice is phishing, which is behind almost a quarter of all data breaches in healthcare. Insider threats make only 7.2% of used hacking methods, with unsecured databases following closely after. The main reason for medical leaks is human error and lack of education amongst employees.
ID Theft and Fraud Complaints Reach Record Numbers

Hackers use stolen records to carry out an array of fraudulent activities and different types of identity theft — and FTC complaints show they do just that. The report from 2020 shows that the agency received almost 4.8 million complaints. Out of those, 1.4 million were noted as fraud and 2.2 million referenced identity theft. This also proves a high influx from previous years, as the FTC received around 1.5 million fewer complaints in previous years.
U.S. losses from identity theft increased by 42%, rising from $502.5 billion in 2019 to $712.4 billion in 2020. Three types of identity theft were most prominent that year: government benefits applications, credit card fraud, and miscellaneous ID theft (like payment or insurance account fraud).
U.S. losses from identity theft increased 42%, rising from $502.5 billion in 2019 to $712.4 billion in 2020. Three types of identity theft were most prominent in 2020: Government benefits applications, credit card fraud, and miscellaneous ID theft (i.e. online shopping/payment account fraud, email/social media fraud, medical/insurance/securities account fraud) accounted for the vast majority of reports.
Which Components Are Vulnerable?
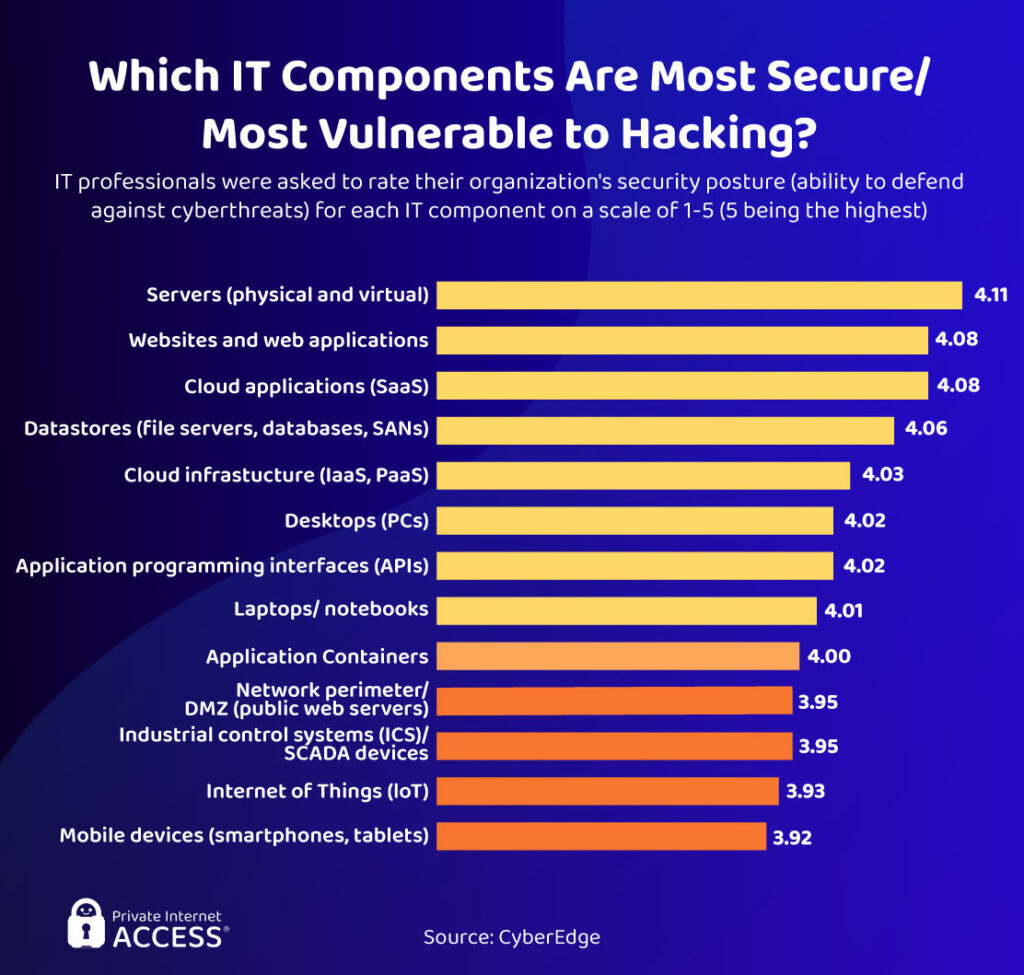
Now let’s take a look at the most vulnerable devices, applications, and systems that hackers can target.
Mobile devices and IoT devices (such as smartwatches, speakers, and AI assistants) have a high risk of being targeted in a cyberattack. That’s because they often have outdated cybersecurity technology or lack protection features altogether. They usually suffer malware attacks from malicious apps or smishing/phishing attempts. IoT devices may also become bots and be used in DDoS attacks.
Mobile devices often have outdated cybersecurity technology (older versions of Android & IOS are particularly vulnerable). They can suffer malware attacks from malicious apps or smishing attempts. In a Verizon study, 90% of companies suffered a mobile device compromise in 2020 and rated the effect “moderate” or worse.
Inadequate IoT
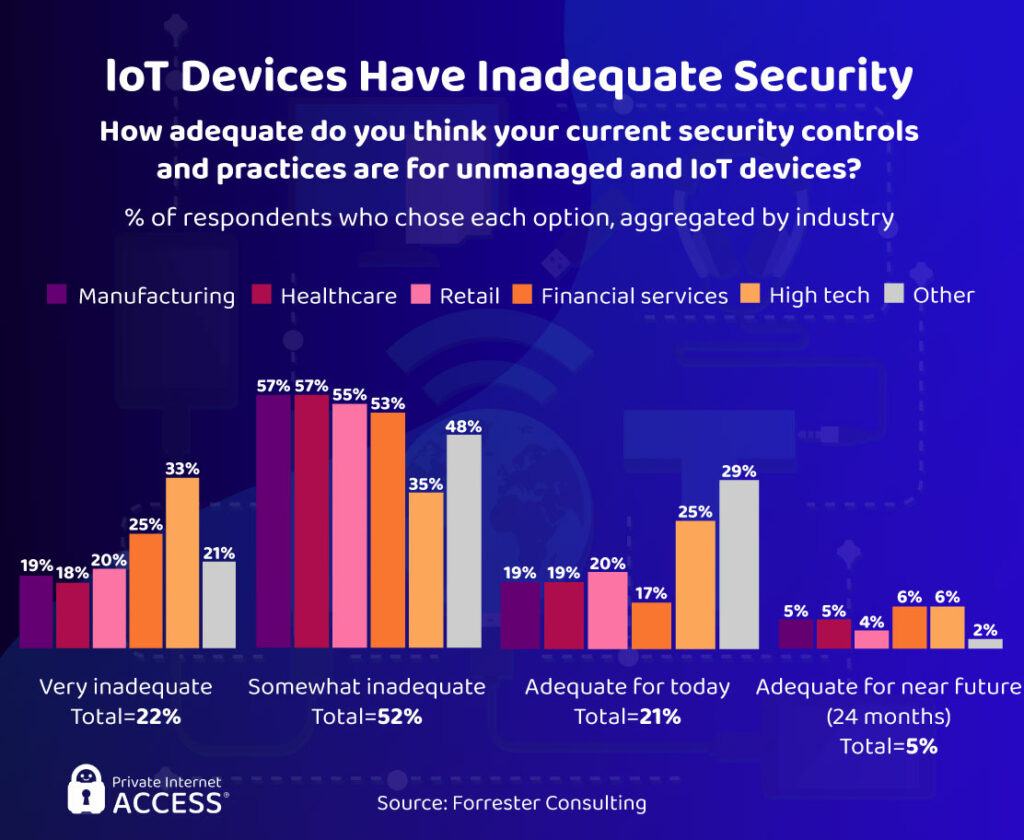
IoT describes the “internet of things” — networks of physical objects interconnected with microchips. This could be smart heart sensors, smart fridges, smartwatches, and so on. Since it’s still so new to the marker, IoT devices are a vulnerable technology. They’re continually unprepared to defend against the threat of hackers. The vast majority of sectors rate their IoT devices as “inadequate” to some degree.
Palo Alto calculates that 57% of IoT devices are potentially vulnerable to hackers. In a Forrester survey, 84% of cybersecurity professionals believe computers are less vulnerable to hacking than IoT. This explains why hackers target IoT devices regularly — and why IoT attacks rose by 35% in 2020 compared to 2Q 2019.
IoT: Areas for Improvement

When it comes to IoT devices, authentication features are the primary area in need of improvement. Without them, it’s simply too easy for hackers to break through the basic (or nonexistent) security. The most effective means of security is two-factor authentication, which automatically stops bad actors from gaining unauthorized access.
Access control and data encryption should be far better too. Too many employees can use company accounts without any monitoring, which allows for human errors or internal threats. IoT devices usually sport very weak to no data encryption, too. That way hackers don’t even have to try hard to get to user files.
Top Mobile Malware

It’s a common misconception that malware affects only PC users, as mobile viruses are equally (if not more) popular among hackers. Mobile malware can be installed on your device through phishing, malicious ads, or even directly through the apps you download. In fact, 99.9% of discovered mobile viruses came from third-party app stores.
Hiddad malware is the no. 1 threat to mobile devices. It’s essentially a Trojan adware that disguises itself inside various in-app promotions. Once installed, the virus hides itself deep within your files, making it difficult to delete, and collects all saved information on your phone.
xHelper, Necro, and PreAMo are the next 3 popular Trojans used by hackers all over the world. Their main aim is the same as Hiddad’s (and other mobile malware), but they sport slightly different disguises. xHelper hides as a cleanup virus, PreAMo is another ad-clicking software, and Necro is a bot that often hides in apps.
Smishing VS Mobile Users
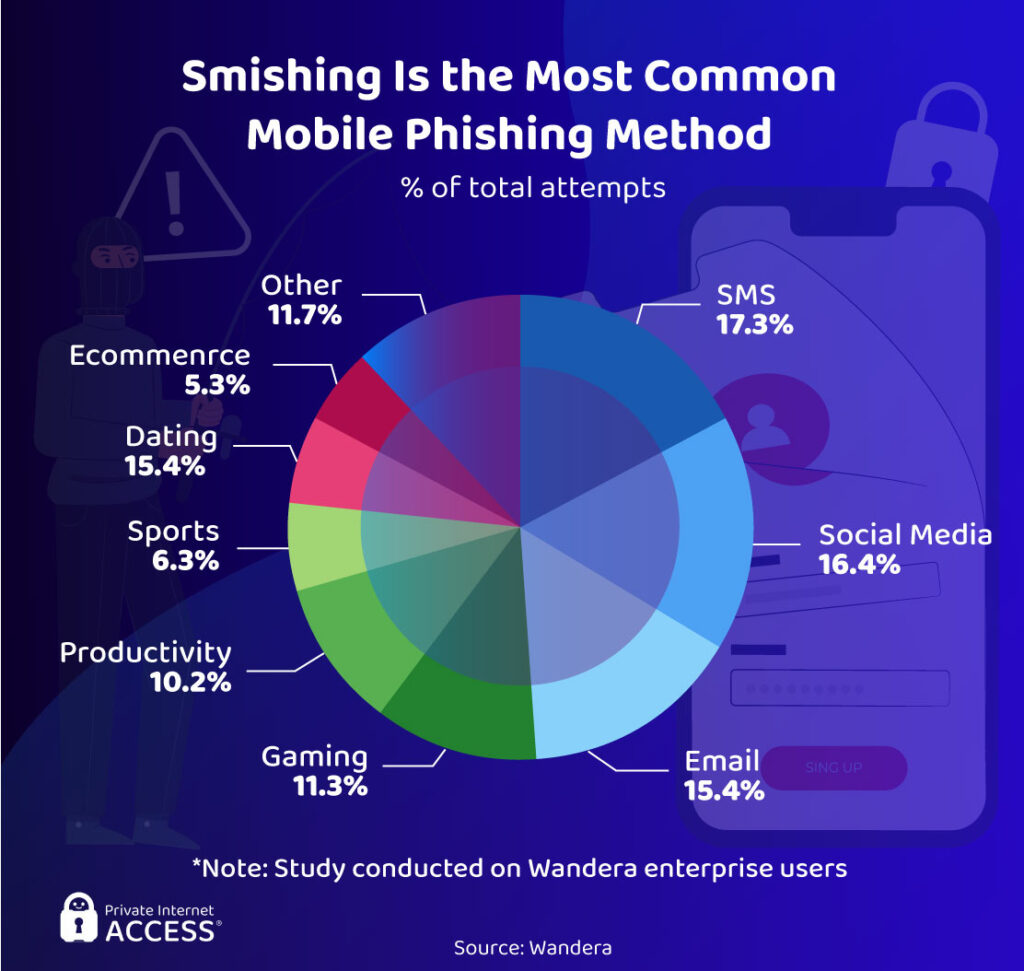
I’m sure you’ve received at least one text that said “Your parcel is arriving. Click this link to track your order.” I know I get it at least once a month. That’s because smishing, also known as SMS phishing, is the most prevalent threat for mobile users worldwide. These frustrating texts now make up for almost 20% of all mobile phishing attacks.
Mobile phone attacks got worse in 2020 as phishers leveraged COVID-19-related attacks, targeting vulnerable users. This led to a 328% increase in smishing attempts. According to NextCaller, 44% of US citizens reported a surge in scam phone calls and texts at the beginning of the pandemic.
Social media and email phishing attacks are the next two big threats for users of phones, tablets, and other mobile devices. Collectively with smishing, they are responsible for almost half of all mobile phishing attempts.
Rising Concerns Around Application Attacks

Web and mobile applications are vulnerable to credential-based attacks and PII harvesting. The biggest concern here is account takeover and credential stuffing, which uses already stolen login details from one site to break into your profiles on other platforms.
Credential stuffing is one of the most popular hacking methods, since many of us use the same and/or similar credentials for multiple accounts — making it easier for hackers to profit loads more from just one attack.
Malicious browser extensions are the 3rd biggest concern around web app attacks. They’re easy to disguise as harmless add-ons, tricking you into installing them directly on your device. But once they’re there, they often cause irreparable damage.
Card and payment fraud is also of concern to IT professionals running web and mobile applications. Considering how much hackers tend to target financial data, it’s not surprising though.
Malicious Apps: More Common Than You Think

Malicious mobile apps are shockingly common. Research identifies over 45,000 malware-riddled apps, with gaming (21%), tools & personalization (20%), and entertainment & lifestyle (17%) categories being the most affected. Almost 30% of malicious programs were found on Google Play, but third-party app stores still pose the biggest risk to mobile users.
In 2020, Secure-D blocked over 1 billion malicious mobile transactions. That’s 95% of all mobile transactions, totaling $1.3 billion. On top of that, 93% of the transactions were stopped because malicious bots were present at checkout. This indicates that hackers are looking for payment details as their attacks are mostly financially motivated.
Web Applications Are Targeted More Than Ever Before

Web applications, for that matter, are a fashionable target for hackers attempting to expose data. Verizon noted that attacks on web applications were part of 43% of data breaches in 2020. That means web apps are targeted twice as often as they were in 2019.
This makes complete sense. As workers moved out of the office and into remote work, the use of work collaboration and networking web applications has increased massively.
Web applications are a fashionable target for hackers attempting to expose data. Verizon noted that attacks on web applications were part of 43% of data breaches in 2020. That means web apps are targeted twice as often as they were in 2019.
This makes complete sense — as workers moved out of the office and into remote work, the use of collaboration and networking web applications has increased massively. Hackers have simply chased users onto the platforms they’re using most.
Stolen credentials and app vulnerabilities were the two primary methods hackers used to exploit web applications. According to Verizon, around 80% of all web app attacks used brute force to get hold of your details. The remaining 20% of attacks were possible due to weak entry points hackers could break through and gather your PII.
Phishing Websites Are Getting Smarter

Phishing sites are becoming more advanced with every passing day. Throughout the past few years, there have been tell-tale identifiers of a secure site. For example, if a domain starts with a “https” or features a padlock symbol, then the website usually has an SSL certificate. This should identify a platform as secure… but does it?
Sadly, that’s not the case. Phishing sites are now simply installing SSL certificates to trick you into believing they’re safe. In fact, more than 85% of phishing sites had an SSL certificate in Q4 2020. This is dangerous as it boosts the effectiveness of phishing sites by authenticating them, to a certain extent, as trustworthy domains.
Why do hackers attack through phishing sites? Because it’s easy. Phishing websites are essentially dupes of legitimate domains, like eCommerce platforms you usually buy from. Since they look identical, they trick you into putting in all of your details, like full name, address, billing data, and more, letting hackers walk away with an abundance of information.
Email: You’ve Got Malware

Email is an easy way for hackers to deliver phishing messages because it’s often readily available. Most people have an email address in plain view on social media sites, especially in a professional capacity. Data breaches leak email addresses all the time, too. It’s no surprise that research shows 75-90% of all malware is distributed by email.
Luckily, there’s an easy way you can protect yourself against phishing attempts — do nothing at all. Over 90% of email phishing attempts require you to take some kind of action, such as click a link or provide information. So, the best way to avoid downloading malware is to just ignore the message, especially if you think the email is suspicious.
Business Email Compromise: Top Subject Lines

Business Email Compromise (or BEC for short) is a specific type of email phishing that targets employees. Why do hackers attack companies? Simple: companies hold a lot more data than regular users, so gaining access to sensitive company files and systems brings in more revenue.
BEC attacks rely on urgent requests, payroll scams, and gift-card scams in 97% of cases. Urgent requests account for 85% of these attempts, with 59% of messages requesting employee help and 26% asking if they’re available. Barracuda found that subject lines referencing financial topics are more common overall. “Payment status,” “purchase,” “invoice due,” and “payroll” all feature in the top 12 phishing subject lines affecting all users.
There are some key differences between BEC attacks and general phishing attempts. The sender of BEC emails always impersonates a senior person in a company, like a CEO or manager. General phishing isn’t this specific as you might receive messages that seem to come from a big retail company, courier, bank, and so on — they never seem to be sent by 1 person.
Why You Should Never Trust Social Media
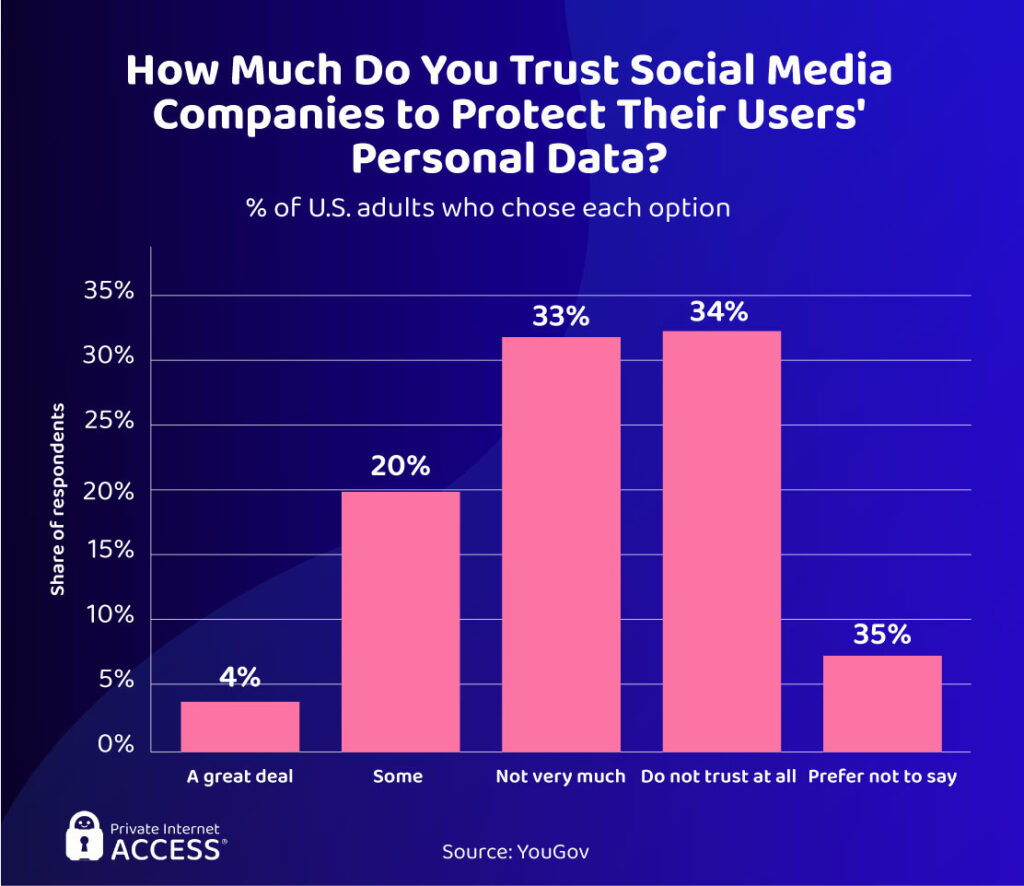
Social media sites have been somewhat of a data privacy nightmare over the last few years.
Social media sites have been somewhat of a data privacy nightmare over the last few years. Users often highlight the intrusive data collection and sharing practices of social media providers and these sites often contain a number of cyber risks. To make it more evident, YouGov statistics prove that 33% of users don’t trust social media a lot — and 34% don’t trust them at all.
There’s a good reason behind it. Phishing messages, fake accounts, and fraud are the biggest threats on social media right now. The RSA’s 2020 report found 500 online groups dedicated to fraud. These groups contained around 220,000 members, 60% of which were on Facebook. Fake accounts are a source of fraudulent malware as 12% of phishing clicks come from social media users, while 20% of malware infections originate from plugins or add-ons.
But perhaps the biggest worry for social media users is that their account credentials may be leaked at any point without their knowledge…
Which Accounts Are Often Compromised?

Billions of user records have been exposed by data handlers over the last few years, with social media being particularly guilty of mishandling customer data. The likes of Facebook, Instagram, Twitter, and LinkedIn all suffered damaging data leaks.
Not too long ago, LinkedIn leaked records affecting 700 million of its users, while Facebook exposed the credentials of 533 million accounts in 2019. Other significant social breaches include Sina Weibo, which compromised 538 million accounts in 2020. Adult Friend Finder’s 2016 leak impacted 412.2 million users with account credentials among the compromised data.
This explains why 51% of account takeover victims had their social media profile broken into. Banking accounts make up 32% of cases and e-messaging services are the third most frequently compromised account, affecting 26% of victims.
Threats to the Public Cloud
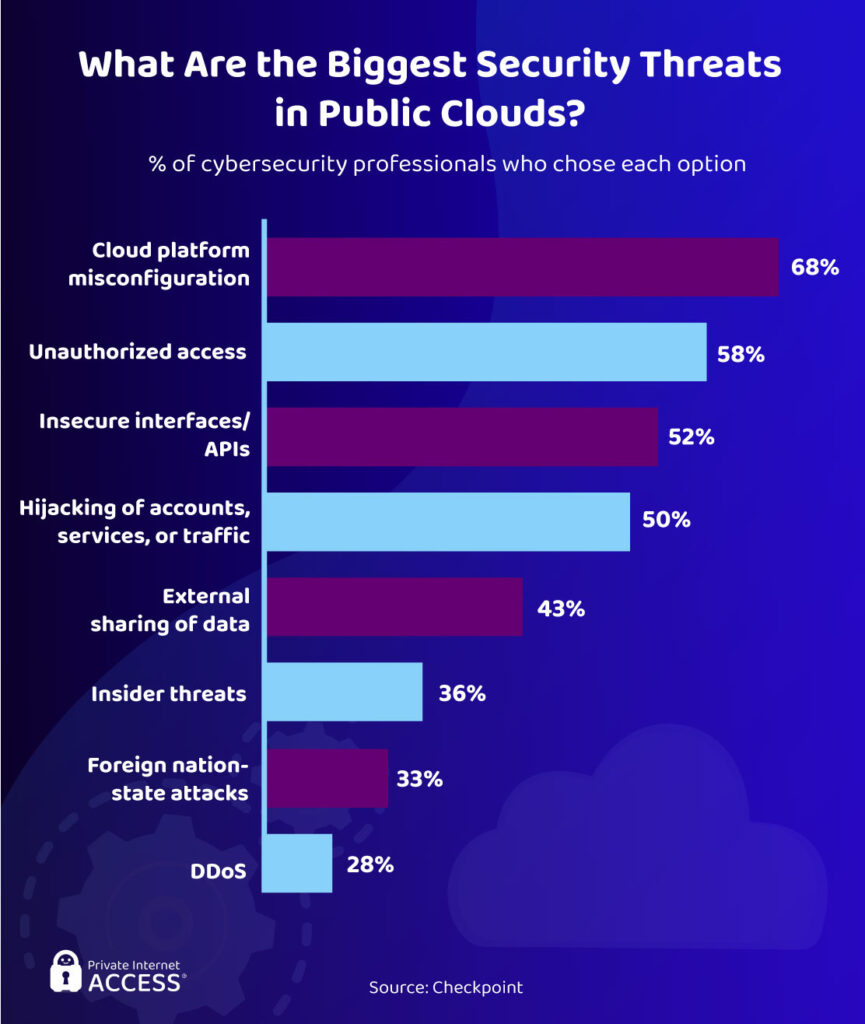
Data collection is becoming customary as businesses move towards greater personalization and AI analytics. Companies usually hire servers from public cloud providers to store all of this customer data. As such, hackers prefer targeting cloud servers and why 75% of cybersecurity professionals say they’re “very concerned” about cloud security.
There’s a distinct lack of qualified cybersecurity professionals and public cloud servers are a relatively new concept for many businesses. The novelty aspect leads to human errors, such as platform misconfiguration, which can provide easy access for hackers and land businesses with hefty data protection fines. No wonder the cloud is a concern.
On top of that, attackers took advantage of vulnerable employees and servers during the onset of COVID-19 and remote work. Cyberattacks on cloud-based data stores grew 630% between January and April 2020. This is only predicted to get worse as more businesses move from in-house work to online systems.
The COVID-19 Effect
If cybercrime wasn’t high enough before 2020, the COVID-19 pandemic has added various additional challenges to businesses and private users. The shift towards remote working has opened up plenty of opportunities for hackers to target web applications and employees on insecure home networks.
Hackers have been able to leverage COVID-19-related scams, and certain sectors have been especially vulnerable to cyberattacks as they focus on adapting to the pandemic. Let’s take a closer look at why hackers hack during the pandemic and the stats relating to the change in the world.
The Increase in Cybercrime During COVID-19

The pandemic prompted a 600% increase in cybercrime, with every threat imaginable surging throughout 2020, from phishing to malware to DDoS attacks. Four out of five chief information security officers (CISOs) say cyberattacks increased because of the boom for remote work.
IBM’s graph shows that hackers chose ransomware more than any other attack type in 2020. According to Deep Instinct, malware attacks soared by a staggering 358% overall while ransomware attacks grew 435% compared to 2019. DDoS attacks increased 55% between January 2020 and March 2021. Their frequency was also up 20% in 2020 compared to 2019.
The shift towards remote work suggests cyberattacks will only continue to rise. According to Malwarebytes, remote workers have been the root cause of data breaches in 20% of businesses.
Remote Work Impacts Cybersecurity

Remote working doesn’t only provide hackers with plenty of targets to exploit, it also increases the time it takes for organizations to respond to a cyberattack.
In an IBM’s study, 54% of organizations required a remote workforce in response to the COVID-19 pandemic. Of these organizations, 76% believe remote work increases the time it takes to identify and contain a data breach. Organizations struggle to identify endpoints with so many employee laptops, computers, tablets, mobiles, and IoT devices in use off- site.
Furthermore, the time it takes to detect a breach is one of the most important factors behind breach costs, second only to the cost of lost business. This is why 70% of organizations think remote working increases the cost of security breaches. IBM found businesses with a remote workforce incurred, on average, $137,000 higher costs per data breach.
Hackers Leveraged Scams and Malware

ENISA researchers identified spam as the most popular threat leveraging the COVID-19 pandemic and related themes. Spam mail accounted for 65.7% of COVID-19 related threats and 26.8% of these emails contained malware. Just in March 2020, scams increased by a whopping 400%. COVID-19 related cyberattacks increased a further 30% in May 2020 compared to April, rising to 192,000 attacks per week.
Google was blocking record numbers of pandemic-related malware and phishing emails, too. The multinational reported 18 million blocked malware emails in April 2020 alone. By the end of the summer, the FBI stated it had seen 12,377 different types of COVID-related scams.
What Malware Did Hackers Use During COVID-19?

Different malware families were “in vogue” at different stages of the pandemic. Ursnif was one of the first malware families used in conjunction with COVID-related scams, but it was Fareit and TrickBot that were more popular during the pandemic. Fareit is a credential-stealer, while Trickbot is a theft/banking trojan. In both cases, what hackers are looking for is your personal details and financial data.
COVID-19 Ransomware, Emotet, and Azorult were the three most damaging malware families leveraging the pandemic. COVID-19 Ransomware was used to hold major organizations to ransom over their data. Emotet sent COVID-related phishing emails to a person’s contacts, and Azronult stole credentials/information when downloaded.
Popular COVID-19 Related Scams and Hacks

By August 5th 2021, the US Federal Trade Commission (FTC) had received over 570,000 complaints of COVID-19 related scams at a total cost of $519 million. Three-quarters of these scams involve fraud or identity theft.
Phishing attempts referencing the COVID-19 vaccine are one of the most common complaints. These messages would imitate big health organizations and reference vaccine coverage, locations to get vaccinated, methods to reserve a vaccine, and vaccine requirements.
Malicious websites also took advantage of people’s COVID-19 fears by offering information on news, testing results, and other resources. Since most of them looked legitimate and trustworthy, people were more likely to believe the information found on these sites. However, many proved nothing but fake platforms created by hackers to infect users with malware or retrieve credentials and card details.
Lastly, unemployment scams exploit vulnerable people by referencing unemployment benefits or the promise of cash. Their only goal is to defraud people and gather a significant amount of data. Sometimes, these scams would even encourage people to pay a lot of money to secure a job — only to ghost a hopeful individual straight after.
Hacks and Vulnerabilities Involving COVID-19 Data

Institutions handling the response to COVID-19 have been the focus of many hacking groups throughout the pandemic. Some organizations were hacked outright, while others had their data exposed through vulnerabilities in their websites or applications.
Hacking groups targeted COVID-19 vaccine research in 2020. The European Medicines Agency (EMA) breach is perhaps the best example of a successful hacking attempt. Hackers accessed files on the Pfizer-BioNTech vaccine stored by the EMA during an evaluation.
Some big vulnerabilities may have allowed hackers access to tonnes of data, too. The PUA breach exposed applicant data through a website vulnerability and the US disaster loans application program leaked PII through its website’s EIDL application portal.
Meanwhile, programmers discovered a dangerous RCE vulnerability in Germany’s Corona-Warn-App – one of many COVID-19 mobile apps found with security vulnerabilities.
Target Industries of COVID-19 Cybercrime

The financial industry was the most targeted sector in 2019 and this didn’t change in 2020. IBM Security X-Force found that 23% of all hacker attacks targeted banks, insurance companies, and other businesses within the money industry.
Elsewhere, the manufacturing (17.7%) and energy (11.1%) sectors ranked as prevalent targets during COVID-19 after being the 8th and 9th most targeted industries in 2019. These are critical industries that were still operating during the pandemic.
Retail was ranked as the 4th most targeted industry, falling from 2nd in 2019. Meanwhile, healthcare rose from 10th in 2019 to the 7th spot in IBM’s 2020 review of cybersecurity incidents.
Spending Increased in Response to the Pandemic

As cyberattacks ravaged numerous industries, businesses had no other option than to increase their cybersecurity expenditures. We see this in the upward trajectory of cybersecurity budgets.
In a CyberEdge survey, 86% of IT professionals claimed their organization was placing greater emphasis on cybersecurity investments. Over 50% believe their business has heavily reprioritized cybersecurity — a significant response to a significant issue. This gives hope that we’ll see a decrease in successful hacking attempts in the future.
This was Part 2 of our Hacking the World series.
Read on for Part 3: Who & Where – The Hackers and the Hacked.
Or check out Part 1: Hacking Basics and Part 4: The Cost & Future of Hacking (Plus: Safety Tips).
Comments are closed.

Hi, a lot has changed due to the covid, thanks for this article