We Need Decoy Operating Systems on Smartphones
Whether it violates the Fourth Amendment of the U.S. Constitution or not, it’s an unfortunate fact that U.S. Customs and Border Protection agents routinely force travelers entering the country to unlock their phone for inspection under the threat of confiscation or prolonged detainment. Thousands of travelers per year are forced to hand over their cell phone passcode/password by agents who sometimes disappear for up to 30 minutes with their phone, doing who-knows-what. In addition to this warrantless violation of privacy, one has to also wonder what other motives agents might have while in possession of your phone. Here in the U.S., there have been an influx of cases in recent years in which police officers were found guilty of planting evidence on innocent people during a search of their vehicle. How long will it be before evidence is planted on someone’s phone during one of these unlawful searches?
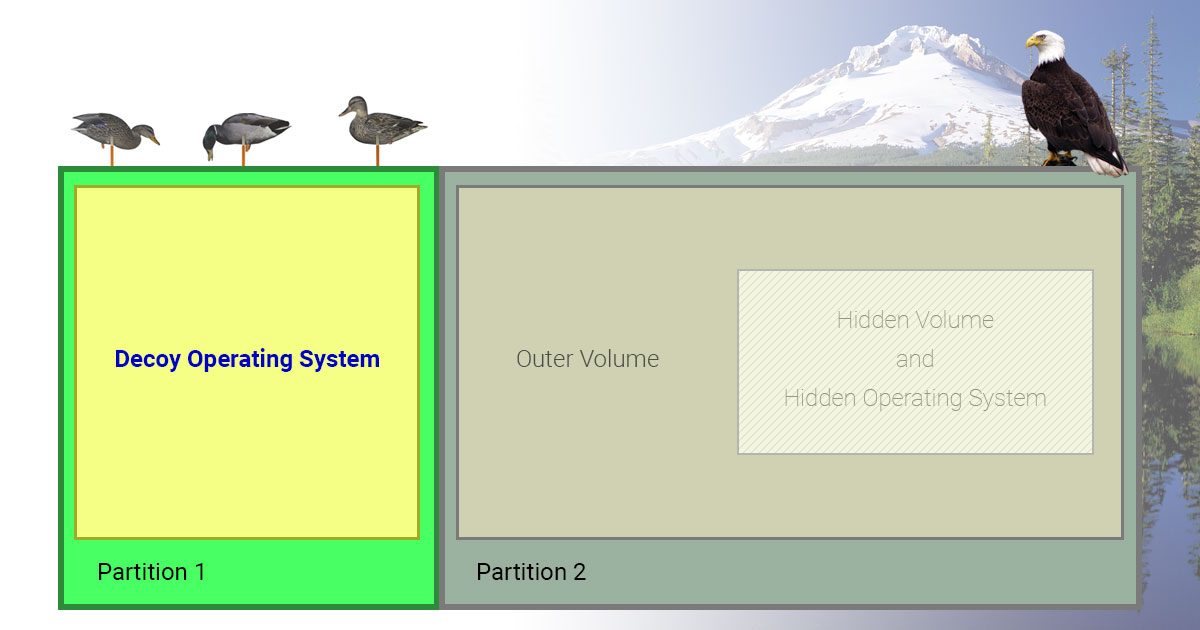
We need phones with decoy operating systems. That’s how VeraCrypt handles this problem with Windows systems. VeraCrypt, a piece of software designed to encrypt files and disks on desktop systems, allows you to set up a system with two boot passwords. One password boots the computer into a decoy operating system and the other boots into a hidden operating system where your real data resides. Advanced techniques are used to provide plausible deniability of the hidden operating system. This means that even if a forensic investigator suspects it exists, it cannot be proven forensically, that it does in fact exist. Finding a way to do this with a mobile device is problematic, however. There are limited options out there for the average person.
The Armadillo phone boasts of a decoy password feature, but it’s quite pricey. It’s designed so that a decoy password displays decoy data and the real password grants access to your real data. In addition, there is a third password that wipes the device, along with a plethora of other sophisticated security features. If an agent forces someone to provide them the password, it would be difficult for the agent to determine whether or not they were just provided the real password or the decoy password. In addition, they wouldn’t know if typing the password they were given, would wipe the device. But the Armadillo is rather cost prohibitive, running $1,295-$1,595 for models which offer the decoy password feature.
This leaves many privacy conscious international travelers with either carrying a burner phone, or backing up and wiping their current phone before travelling. These solutions are not perfect. A burner phone or wiped phone could in some cases have recent call history or other information that would be disclosed to federal agents performing unlawful searches. As you can see, there is a gap here as far as what is needed by the average individual and what’s available to them. Earlier this month, New Zealand passed the Customs and Excise Act 2018, which imposes a fine of over $3,000 to travelers unwilling to unlock their phone for Customs agents. If other countries follow suit, things could get worse.
Requiring this extreme level of transparency of average people seems lopsided, especially coming from governments like the U.S. whose spy agencies have become increasingly opaque in recent years as clandestine operations are expanded around the world. If the average person must be willing to grant the state access to their every personal communication, shouldn’t powerful politicians in Washington be required to show the people the same? But wealth and power are above transparency. They are assumed innocent until proven guilty, while the average person is considered guilty until proven innocent. The Constitution and natural law be damned. You must be electronically strip-searched by the surveillance state.
It would be much harder for governments to pull this off if more citizens actually viewed mass surveillance as unethical. But politicians are masters at driving their agenda through fear, convincing the masses that terrorism will be at their doorstep if they don’t turn over their privacy and ultimately their dignity to authority. Here’s hoping that more options for smartphone privacy will arrive on the scene, defending privacy-conscious individuals from these warrantless phone searches.
