How to Use Private Internet Access and Tor: Tor over VPN or VPN over Tor?

A big question for those who consider internet privacy essential is how to best use Tor in combination with a VPN service provider like Private Internet Access. Should a Tor connection be tunneled inside an already established VPN connection, or should a VPN connection be tunneled inside an already established Tor connection? Before you can answer these questions, however, you must first consider your threat model.
TL;DR – In most situations, you are going to want to use User > VPN > Tor
This article assumes that the user is using good operational security that will not out themselves while on the network. Opsec is a set of best practices for remaining private while using anonymity networks. For more information about tor and VPN opsec, see our article next Wednesday.
Let’s discuss two main threat actors:
1. An oppressive regime
2. A malicious VPN service provider
The first of these is obvious, but the latter is of course ironic. However, we understand you may be in a position where you can’t afford to completely trust anyone – even us. That’s where equipping you with information can give you the ability use the service effectively without having to trust us with your raw data streams.
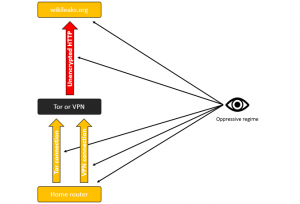
We’ll start with the first threat actor shown above. Oppressive regimes quite commonly have the ability to view traffic as it travels across ISP (internet service provider) infrastructure. If you are connecting to Tor or a VPN service from home, this means an oppressive regime can see your home IP address connecting to an IP address associated with Tor or the VPN. However, since your traffic to Tor or the VPN is encrypted, they theoretically (unless you have already been compromised in some other way) can only observe that you are connecting to Tor/VPN and not decrypt the actual encrypted traffic itself. Once your traffic has passed through the Tor or VPN connection, it needs to egress to its final destination, like wikileaks.org, perhaps. During that final leg of its trip, the traffic will no longer be tunneled through the Tor or VPN connection. Your traffic is now more susceptible at this point to the snooping of an oppressive regime. Not only will the egress IP address associated with Tor or the VPN service be visible, but the final destination IP address will also be visible. In addition, since your traffic has now egressed from the encrypted tunnel, if you use an unencrypted protocol like HTTP (not HTTPS/SSL), the oppressive regime can snoop on the full content of your traffic.
What an oppressive regime could be targeting in this threat model:
- The full content of traffic going over unencrypted protocols like HTTP (not HTTPS/SSL)
- The fact that you connected to Tor
- The fact that you connected to a VPN service
- The IP address of your home router, yielding your physical location
- The IP address of your traffic’s final destination
Figure 1 – What an oppressive regime can see when you are using only Tor or only a VPN
You can generally eliminate A by only browsing to sites which use SSL (HTTPS), though there can be complexities. It’s impossible to avoid both B and C at the same time in most common scenarios (more detail later). It’s also impossible to avoid D and E, but the use of Tor or a VPN is of course designed to make it impossible to tie D and E to one another in this threat model.
Now let’s talk about a malicious VPN service provider. This threat actor can also target A through E but with advantages an oppressive regime does not have: Firstly, they can tie D and E to one another. This is why it’s so important to choose a VPN service provider that does not use any logging and is willing to shut down operations in a specific nation if that nation makes demands that users’ identities be logged. Secondly, if you used a payment method which identifies you, they know who you are. How can you protect yourself from a malicious VPN provider then? This is where the strategy of using Tor in concert with a VPN service comes in. Let’s drill down into the ramifications of each of the two methods.
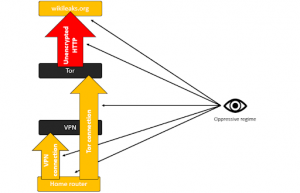
User > VPN > Tor
In this configuration, the user first connects to the VPN service, then to Tor. This allows you to hide the fact that your home IP address is connecting to Tor but requires trusting your VPN provider who can see the connection to Tor. Below is more detail on the threat models.
Oppressive regime
What they can see:
- The full content of traffic traveling over unencrypted protocols like HTTP (not HTTPS/SSL)
- The fact that you connected to a VPN service
- The IP address of your home router, yielding your physical location
- The IP address of your traffic’s final destination
What they CAN’T see:
- They cannot tie the IP address of your home router to the IP address of your final destination
- The simple fact that you connected to Tor
Malicious VPN provider
What they can see:
- The IP address of your home router, yielding your physical location
- The fact that you connected to Tor
What they CAN’T see:
- The full content of traffic going over unencrypted protocols like HTTP (not HTTPS/SSL)
- The IP address of your final destination
- Your traffic stream, because it is being encrypted by Tor
User > Tor > VPN
This configuration is more difficult to set up. The user first connects to Tor, then to the VPN service. This configuration can be very risky as far as your VPN provider identifying who you are. On the other hand, it allows you to not be flagged by the sites you visit as being a Tor user.
Oppressive regime
What they can see:
- The full content of traffic traveling over unencrypted protocols like HTTP (not HTTPS/SSL)
- The fact that you connected to Tor
- The fact that a Tor connection connected to your VPN account
- The IP address of your home router, yielding your physical location
- The IP address of your final destination
- If your VPN username was previously used to connect from home without Tor
What they CAN’T see:
- They cannot tie the IP address of your home router to the IP address of your final destination
- The fact that you connected to a VPN service
-
Combined Threat Model
Now, what if we combine both threat models into one? What if the same oppressive regime controls not only the ISP but also the VPN service? Here’s how that would look:
User > VPN > Tor
In this case, the combined threat model risk can still be mitigated.
Oppressive regime AND Malicious VPN
What they can see:
- The full content of traffic traveling over unencrypted protocols like HTTP (not HTTPS/SSL)
- The fact that you connected to a VPN service
- The IP address of your home router, yielding your physical location
- The IP address of your final destination, yielding your internet browsing
- The fact that you connected to Tor
What they CAN’T see:
- They cannot tie the IP address of your home router to the IP address of your final destination
User > Tor > VPN
In this case, the defense against the combined threat model is very poor and adds risk.
Oppressive regime AND Malicious VPN
What they can see:
- The full content of traffic traveling over unencrypted protocols like HTTP (not HTTPS/SSL)
- The fact that your VPN user account connected from Tor
- The IP address of your home router, yielding your physical location
- The IP address of your final destination
- The simple fact that your VPN user account connected from Tor
- Who you are (if you used a payment method which is tied to your identity)
- If your VPN username was previously used to connect from home without Tor
What they CAN’T see:
- They cannot tie the IP address of your home router to the IP address of your final destination
It should also be noted that it may possible for an oppressive regime to attempt to use advanced techniques to correlate your ingress traffic (into Tor/VPN) with your egress traffic, though this particular attack is outside of the scope of this article and may be covered in more detail in a future publication.
Figure 2 – What an oppressive regime who has compromised a VPN provider can see in the following configuration: User > VPN > Tor
For those with extreme privacy needs, it can be a complex threat landscape, with considerations that may differ from situation to situation, or even day to day. In most situations, however, the best choice for those wanting to use Tor in concert with a VPN service seems clear: User > VPN > Tor
Stay safe out there!
For a more information, please see our Helpdesk article “Can I Use Tor with the Private Internet Access Service“