RainClouds – The Case Against Cloud Computing Security

In the computing world, there’s always a new buzzword or trend that everyone chases as the next “big thing.” Software Defined Networks (SDNs) will replace most network technicians. Augmented Reality will be a part of our daily lives. Everyone will have a 3-D TV by 2020. Who needs an audio jack on their phone? Quantum Computing will ruin everything. The new TickleMe Elmo features Blockchain technology. The AI powering the next generation Internet of Things will change the world.
While most of these things are gross exaggerations or just outright wrong, there’s a single buzzword that you hear daily in the IT world that alarms me more than any other. The cloud. More specifically, the secure cloud.
The concept of cloud computing is rather simple. You don’t need to build physical hardware for every little task that you need completed. You can split your server into small isolated pieces and divvy up the computing power to many small tasks. The easiest example is the web server. Most websites do not get enough traffic to warrant their own dedicated server, and spending $50 per month on a dedicated server for a website feels like a waste. Cloud technology can break a single big server up into 20 websites, and charge $5/month for hosting the website. The web admins get their website for 1/10th the price, and the web hosts running the servers double their revenue for each server. Everyone wins.
So while the benefits are obvious, looking at the cloud from a security lens is a mountain to overcome. You need to ensure that the hardware is properly isolated, and that the software behaves the same way in the cloud as is expected. If the software crashes, deviates, or is intentionally malicious, the other members of the cloud have to be safe and performing normally. This means that not only do all of the members have to be secure from one another, they have to have the proper resources available, even when other members of the cloud are misbehaving.
These are monumentally complex problems, with billion dollar companies and a whole new concert of buzzwords. Isolation, Sandboxing, Virtualization, Deterrent Controls, Hypervisor, Xen, VMware, Instancing.
But there are fundamental problems with the approaches to fixing the cloud computing problem. Software is inherently insecure, and adding complexity to software invariably adds bugs and anomalous behavior. Hardware design, especially secure hardware design, is a constantly moving target and new attacks come to life on a near-daily basis.
There’s no dancing around this issue. Cloud computing is inherently less secure than regular computing. For every major bug in Linux, OSX, or Windows, you are layering more problems onto your systems by adding the Cloud.
So if you’re a hardware manufacturer, a cloud OS developer, or a host trying to maximize your returns on your hardware, how do you correct this issue?
You conspire.
You try to convince the world that the Cloud is secure, and that you don’t have to worry about outside parties accessing your private data or crushing your services to rubble.
Some marketing materials from three of the biggest cloud computing companies:
 Security security security. Don’t worry, they’ve got you covered. Except they don’t. There are escapes (breaking out of your cloud into other’s on the same computer), RCE’s (remotely breaking into anyone’s cloud who is using a specific platform), and all kinds of information disclosure vulnerabilities. These are not rare occurrences and some of these vulnerabilities cannot be fixed with patching.
Security security security. Don’t worry, they’ve got you covered. Except they don’t. There are escapes (breaking out of your cloud into other’s on the same computer), RCE’s (remotely breaking into anyone’s cloud who is using a specific platform), and all kinds of information disclosure vulnerabilities. These are not rare occurrences and some of these vulnerabilities cannot be fixed with patching.
Let’s take a look at known vulnerabilities for Vmware products:

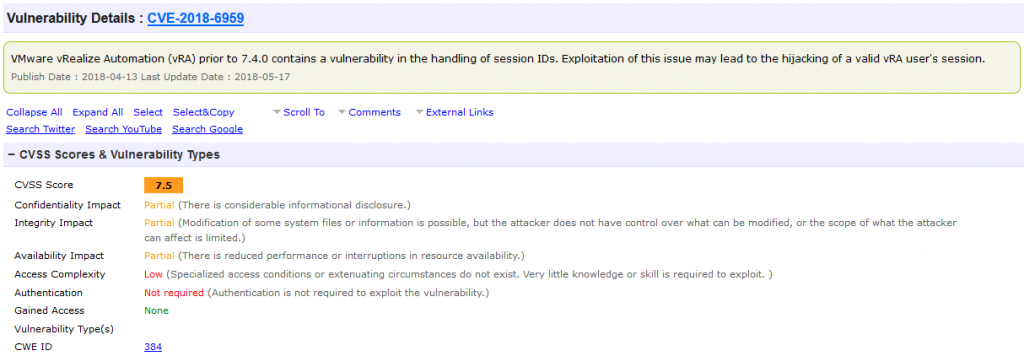

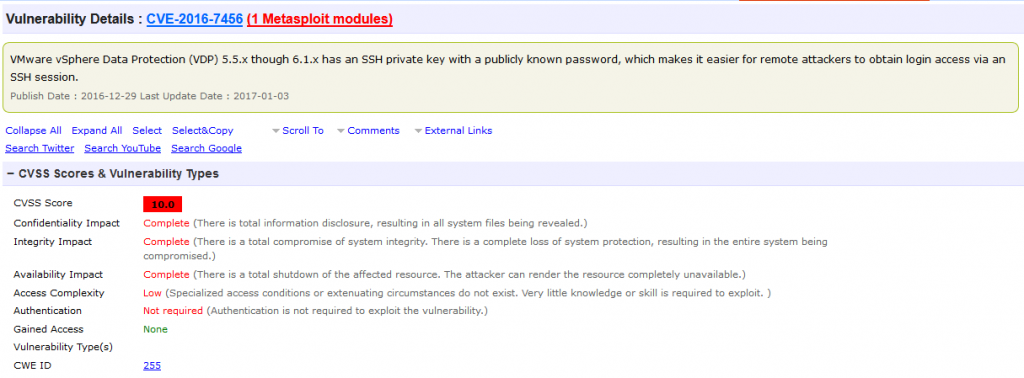 These are the worst kinds of vulnerabilities. Escapes, remote code execution, full information disclosure, hard coded passwords. You may assume that this is a problem at VMware, but this is an industry-wide problem that the “Secure Cloud” faces. The massive amount of complexity added simply makes the systems less secure. You’ll find the same problems with Azure, Xen, and all of the others.
These are the worst kinds of vulnerabilities. Escapes, remote code execution, full information disclosure, hard coded passwords. You may assume that this is a problem at VMware, but this is an industry-wide problem that the “Secure Cloud” faces. The massive amount of complexity added simply makes the systems less secure. You’ll find the same problems with Azure, Xen, and all of the others.
And this is not even considering the significant number of attacks against the hardware itself. Shared resources are particularly vulnerable to hardware analysis and manipulation. Things like Rowhammer, timing analysis, poor security of caches and memory are all problems that the industry seems unable to fully solve.
This week, we have TLBleed, where the translation lookaside buffer in pretty much all Intel processors is compromised and will not be patched. Over the last two months, we have had multiple waves of flaws under the Meltdown and Spectre umbrella that significantly weaken the security of Cloud systems. Rowhammer allows direct manipulation of DRAM from neighbors on your server hardware.
This is why serious security and privacy companies invest in bare-metal hardware for their critical infrastructure. Eliminating the Cloud from your network significantly reduces your attack surface and increases performance.
Remember: The words “secure” and “Cloud” never belong together.
Ask your VPN provider if they use virtual servers or clouds for their VPN network, or if they run bare-metal servers.
Comments are closed.

I think you may be conflating hypothetical security risks with actual security of a given cloud-hosted subsystem. I work in security at a company having hybrid architecture — some bare metal, some in the cloud (AWS). First, I think we can agree that security does not happen without active and aggressive action on the part of the site owner. I would definitely agree that anyone thinking AWS or others do this for you is patently absurd and dangerous, and indeed, the sheer ease that cloud enables makes it “too easy” for naive users to spin up insecure environments. But in a professionally managed system, we have found it much, much easier to manage security using best practices with AWS because there are a large number of tools that are on by default to help identify issues. It’s not that we cannot run similar tools in bare metal, but that practically, we make risk/resource tradeoffs in all aspects of systems management. You may argue that this kind of tradeoff is stupid or unwise, but having worked in this industry for 30 years, I can say that I have never seen a company work any differently. That is, humans are always complicit in security decisions, like it or not. A hypothetically secure (or more secure) system is a fine exercise, but a practically secured environment is our simple human reality. Because AWS is largely automated, and very aggressive with security, we have found they consistently beat our internal Ops team at providing layers and layers of security.