The Internet Cannot be Trusted – Beamsplitters, Backdoors, and Broken Promises

We all know that the Internet is not a fundamentally safe place. With the tremendous gains in information sharing and the conveniences that the Internet brings, come opportunities for exploitation. Fraud, harassment, surveillance, censorship, social and political manipulation, industrial and political espionage, data theft and discrimination have all taken hold in one of the greatest tools ever created by mankind.
This article is intended to show you those failings in design, and the challenges ahead that engineers around the world have to imagine their way out of. I will focus heavily on network equipment, but this problem extends far beyond that horizon. PCs, mobile devices, industrial systems, the cloud, and databases around the world all face serious issues that beyond the scope of this writing.
A little history:
As the Internet sprang to life in the 80s and 90s, some companies rose to the top as market leaders in their particular fields. Cisco Systems are the kings of networking, although their leadership in wireless networking, switching, routing, and firewalls is diminishing over time. Juniper, Arista, Huawei, and a huge number of other small to medium competitors have risen up to challenge Cisco’s dominance over the core functions of the Internet.
I will talk a lot about Cisco here, because they are the market leaders. This problem spans every one of their competitors as well.
Cisco’s Position on the Encryption Debate:
Cisco builds surveillance capabilities directly into its hardware, which it calls “Lawful Intercept.” The idea is that a firm using Cisco equipment can give access to law enforcement to conduct investigations, presumably with some form of due process and a court order. Here is some documentation on how to set up Lawful Intercept on your Cisco equipment. More Info.

And some info on what Lawful Intercept actually does:
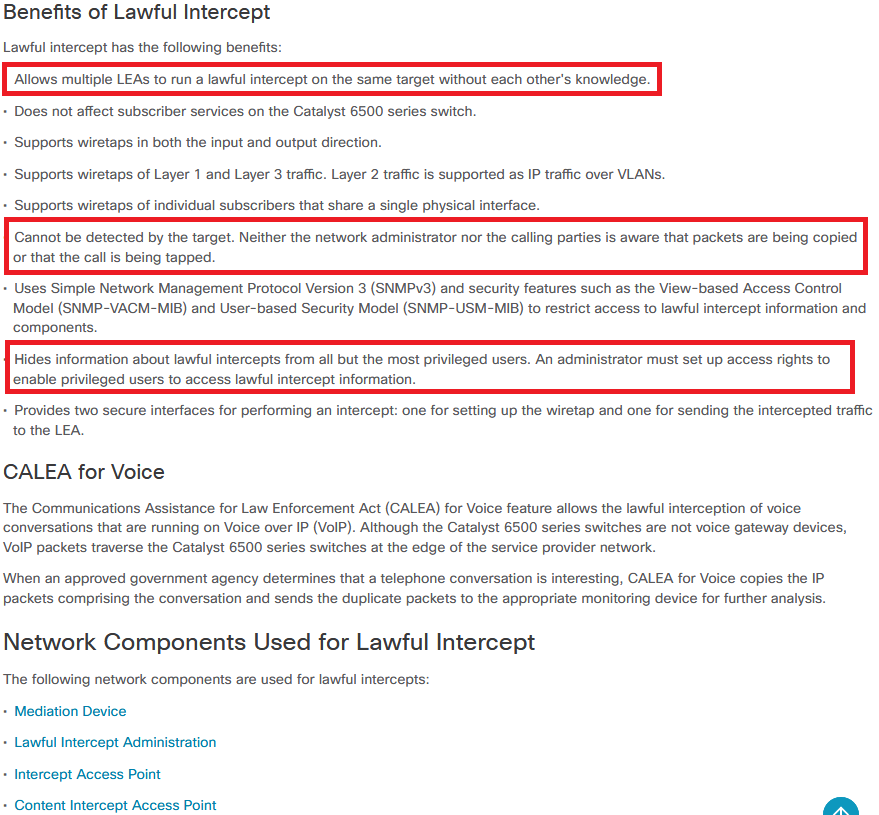
You’ll notice that the language in the documentation repeatedly touches on a problem. Lawful Intercept is intended to be used by law enforcement or government agents who have a legal basis to be conducting surveillance. As with everything in the computing world, making assumptions about how users will access your systems leads to problems.
Problem #1: Access Isn’t Limited in any Meaningful Way
Anyone with access who knows how to setup Lawful Intercept can wiretap people on their network. There are no controls, certificate systems, or other restrictions to prevent access.
Problem #2: Over 150 Security Flaws that can give Hackers Access
Here is a list of security problems for Cisco IOS. Ignoring DoS because that doesn’t actually give anyone access, there’s a long list of serious issues that include gems such as:
Remote users can log into to router with full admin powers using a hard-coded username and password.
In total there are 5 major “full control” flaws in Cisco’s IOS just in the first half of 2018.
What this adds up to is that clandestine agencies are having a field day with the gear that powers the Internet. You’ll see similar serious problems with other major brands of network equipment as well.
How are these problems exploited?
It depends on what your attacker wants. The NSA (and presumably others) have manipulated BGP traffic to intercept and manipulate data. It is also safe to assume that with these kinds of serious flaws at their disposal, one can monitor any counterparty that they wish. We also know a that the NSA stores away the metadata of targets to monitor their activity, and will even store away encrypted data from https websites and end-to-end encrypted services with the hope that the tech will arise to break the encryption at a later time.
What can we do?
It is a long and bumpy road ahead. Router operating systems must be open sourced. It is the only way that you can enable peer-review of code and allow the public (and the company’s customers) to verify that the software powering their equipment is safe, and that a malicious user can’t log into their device with
user:cisco
pass:
…and get admin access to their core networking systems.
The light provided by open-sourcing the software immediately removes the possibility of these kinds of flaws from surfacing. It gives the world reassurance that these systems can be trusted.
Even if we were to switch to PCs to provide networking services like Cisco and Juniper equipment does now, those PCs run on closed-source firmware that cannot be trusted. The Intel Management Engine and AMD Platform Security Processor are both black boxes of code with the highest level of security access to a computer, and the ability to communicate over networks with no operating system even installed on the PC. In the case of Intel Management Engine, it can even work while the computer is powered off if it is plugged in. Extensive research has gone into whether Intel ME can be fully removed, but so far we can only disable it.
Until the day arrives that we can trust our computers and networks once again, we need to encrypt encrypt encrypt. Use a reputable VPN provider. Do not visit web pages that are not https (Let’s Encrypt has made this so easy that there aren’t really any excuses anymore). Encrypt your messages and emails, and don’t trust the equipment that sits between you and the person you are communicating with.
