WireGuide: All about the WireGuard VPN protocol
WireGuard® is a relatively new VPN protocol when compared with the decades old OpenVPN and approaches software development with a different philosophy – do one thing simple and do it well (efficiently). This is known as the UNIX philosophy. WireGuard is licensed under various open source licenses such as GPLv2 – which is the same open source license that the Linux kernel uses. As such, it should be no surprise that WireGuard will be added to the Linux kernel itself – which means WireGuard will eventually be available “preinstalled” on all Linux distributions. The comment that really validated WireGuard’s future ubiquity came from none other than Linus Torvalds. In August of 2018, he mailed the Linux kernel mailing list with this positive comment:
“Can I just once again state my love for it [WireGuard] and hope it gets merged soon? Maybe the code isn’t perfect, but I’ve skimmed it, and compared to the horrors that are OpenVPN and IPSec, it’s a work of art.”
Private Internet Access has been a donor to WireGuard since 2018. This new VPN protocol has been on PIA’s radar for years and we want to share all the reasons why.
WireGuard’s founding marks a new age for VPN
Jason Donenfeld first started working on WireGuard around 2016 with the first release being on December 9th, 2016. At its core, WireGuard is a kernel virtual network interface for Linux that is meant to replace the use of userspace networking on Linux such as tun devices and IPSec. In fact, IPsec has largely fallen out of use in favor of the current industry standard, OpenVPN – which operates in user space using a tun device. WireGuard can also work as a replacement for OpenVPN. WireGuard, in Jason’s own words, is a “solid engineering solution that is both more practical and more secure.” With that in mind, it is still important to note that WireGuard has only recently been released as a stable v1.0.
What makes WireGuard different?
VPN on layer 3 makes things more efficient
One key component that makes WireGuard different than other VPN protocols such as OpenVPN, IPSEC, L2TP, and PPTP is the layer at which it functions. The traditional VPN protocols that most people are familiar with operate at the user level using TLS. In comparison, WireGuard on Linux based VPN servers operates inside the kernel’s networking stack, and there are many benefits to that. The big two are that WireGuard becomes easier to implement and that the authenticity and attributability of the packets are better ensured. WireGuard supports both IPv4 and IPv6 IP addresses, as well as the ability to encapsulate IPv4 packets in IPv6 as well as the other way around. WireGuard uses “cryptokey routing,” so every IP address allowed on the VPN has an associated public key. WireGuard also provides guaranteed perfect forward secrecy.
Less code makes WireGuard more auditable
A notable outcome of WireGuard’s philosophy is that there are fewer lines of code in WireGuard’s codebase when compared with OpenVPN’s. How much less? Two orders of magnitude less – 4,000 lines of code in WireGuard versus over 400,000 lines of code to fully utilize OpenVPN or IPSEC. This means that WireGuard’s codebase has less room for something to go wrong. It also means that WireGuard doesn’t come with the bells and whistles that many have come to expect from OpenVPN such as cipher negotiation – but that is a design choice. Many of the bells and whistles that VPN users are used to can be added on top of WireGuard. Open source code is meant to be built upon. In summary – WireGuard is a simpler, cleaner, and more up-to-date way to connect computers using virtual private tunnels into a virtual private network.
Better cryptographic algorithms and crypto versioning limit impact of vulnerabilities
Instead of using AES or SHA for encryption or hashing, WireGuard uses a bunch of newer algorithms in conjunction. These algorithms, as described on the WireGuard website, are:
- ChaCha20 for symmetric encryption, authenticated with Poly1305, using RFC7539’s AEAD construction
- Curve25519 for ECDH
- BLAKE2s for hashing and keyed hashing, described in RFC7693
- SipHash24 for hashtable keys
- HKDF for key derivation, as described in RFC5869
The icing on the cake though, is the lack of cryptographic agility. Cryptographic agility is the ability for a protocol to swap out encryption algorithms in the event that one becomes obsolete – the mere existence of cryptographic agility opens the door to downgrade or even man-in-the-middle attacks. Instead of cryptographic agility, WireGuard opts to go for crypto versioning – if one of the algorithms mentioned above becomes obsolete, all WireGuard has to do is release a new version to upgrade and leave the vulnerability behind in its entirety and take away the opportunity for downgrade attacks. As Jason explains in his seminal paper introducing WireGuard:
“It [WireGuard] intentionally lacks cipher and protocol agility. If holes are found in the underlying primitives, all endpoints will be required to update. As shown by the continuing torrent of SSL/TLS vulnerabilities, cipher agility increases complexity monumentally.”
Setting up Private Internet Access to try WireGuard
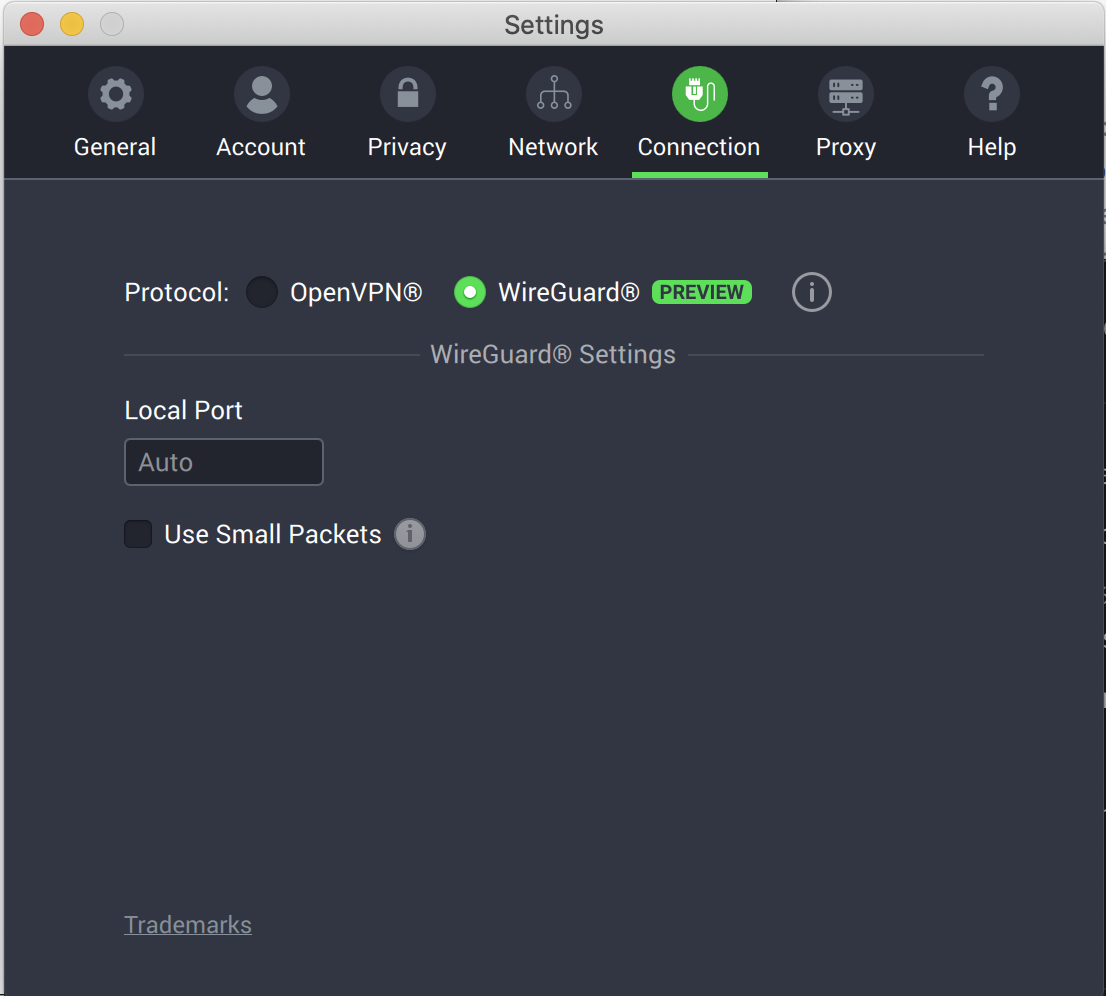
Back when PIA first released WireGuard, to start using WireGuard with Private Internet Access, you needed to be part of the PIA beta program. Now that WireGuard functionality is out of beta, all PIA clients and apps can use this new VPN protocol. Once you have updated your client or app, simply navigate to the Connection tab in the Settings window of your Private Internet Access desktop client or the Protocol section in the VPN Settings of your Private Internet Access mobile app and switch from OpenVPN to WireGuard. Once you do so, you’ll notice less VPN options to choose from. The simplicity of using WireGuard instead of OpenVPN leads to much less option paralysis. WireGuard just works – and beneath the hood is much more efficient.
“WireGuard” is a registered trademark of Jason A. Donenfeld.
Comments are closed.

GCM256 and RSA4096 is runing abou 100 and 100 mb/s
Wireguard is running about 60 70 mb/s to the same server.
This seems backwards or is this normal at his time?